Welcome to the Inedo Forums! Check out the Forums Guide for help getting started.
If you are experiencing any issues with the forum software, please visit the Contact Form on our website and let us know!
NPM Vulnerability with Exception
-
We ran into an issue when a NPM package has a vulnerability, but an exception has been made to allow the package download. The example we have was
static-evalv 2.1.1We have an exception on the PGV-2133354 vulnerability since it has been withdrawn.
npm auditandnpm installfail because the severity level of the vulnerability with exception isinfowhich is not a supported level by NPM. the output from npm is:npm ERR! undefined is not iterable (cannot read property Symbol(Symbol.iterator))NPM Audit Severity Levels
And you can see in the NPM Audit code that it does not expectinfoas a severity levelOutput from ProGet npm/v1/security/advisories/bulk endpoint:
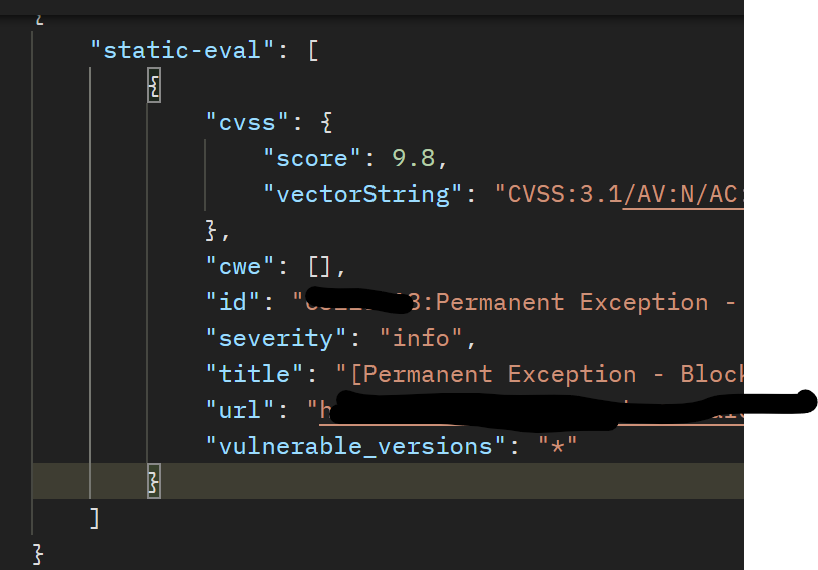
Right now we are NOT able to build with this package without disabling vulnerability detection, which is not permitted by corporate policy. How can we correct the output from ProGet so that npm will successfully build
-
Hi @dan-brown_0128 ,
Thanks for the detailed analysis; we'll get this fixed via PG-2636 in 2024.1 (due later today).
You should be able to assess it as "Low" to work-around it in the meantime. FYI, here is the code that is used to map a vulnerability to an npm vulnerability:
//assessed if (vuln.Severity_Code != null) { return vuln.Severity_Code switch { Domains.AssessmentSeverityCodes.Error => npmAuditSeverity.critical, Domains.AssessmentSeverityCodes.Warning => npmAuditSeverity.high, Domains.AssessmentSeverityCodes.NotApplicable => npmAuditSeverity.info, Domains.AssessmentSeverityCodes.Custom => npmAuditSeverity.info, _ => npmAuditSeverity.info }; } // unassessed and has a Severity Score else if (!string.IsNullOrWhiteSpace(vuln.ScoreSeverity_Text)) { return vuln.ScoreSeverity_Text switch { nameof(CVSSRange.Low) => npmAuditSeverity.low, nameof(CVSSRange.Medium) => npmAuditSeverity.moderate, nameof(CVSSRange.High) => npmAuditSeverity.high, nameof(CVSSRange.Critical) => npmAuditSeverity.critical, _ => npmAuditSeverity.info, }; } return npmAuditSeverity.none;Thank you,
Steve
-
The vulnerability has already been assessed as "Not Applicable" and that's where the "info" comes up, as shown by your code snippet. The problem is that NPM does not have info as a classification and cannot parse it
-
@dan-brown_0128 I understand
So you'd either have to upgrade (where we fixed the code) or reassess it to Low so npm audit won't crash. I suppose you could also patch npm audit so it doesn't crash.