@atripp said in Problem with PGV-22381O7 (tree-kill1.2.2 incorrectly flagged vulnerable):
Anyway, ISL is managed by a different team, so I'll submit an internal request to review. It doesn't seem so urgent, just inconvenient/incorrect and easy to workaround in ProGet. But let me know if I misread that.
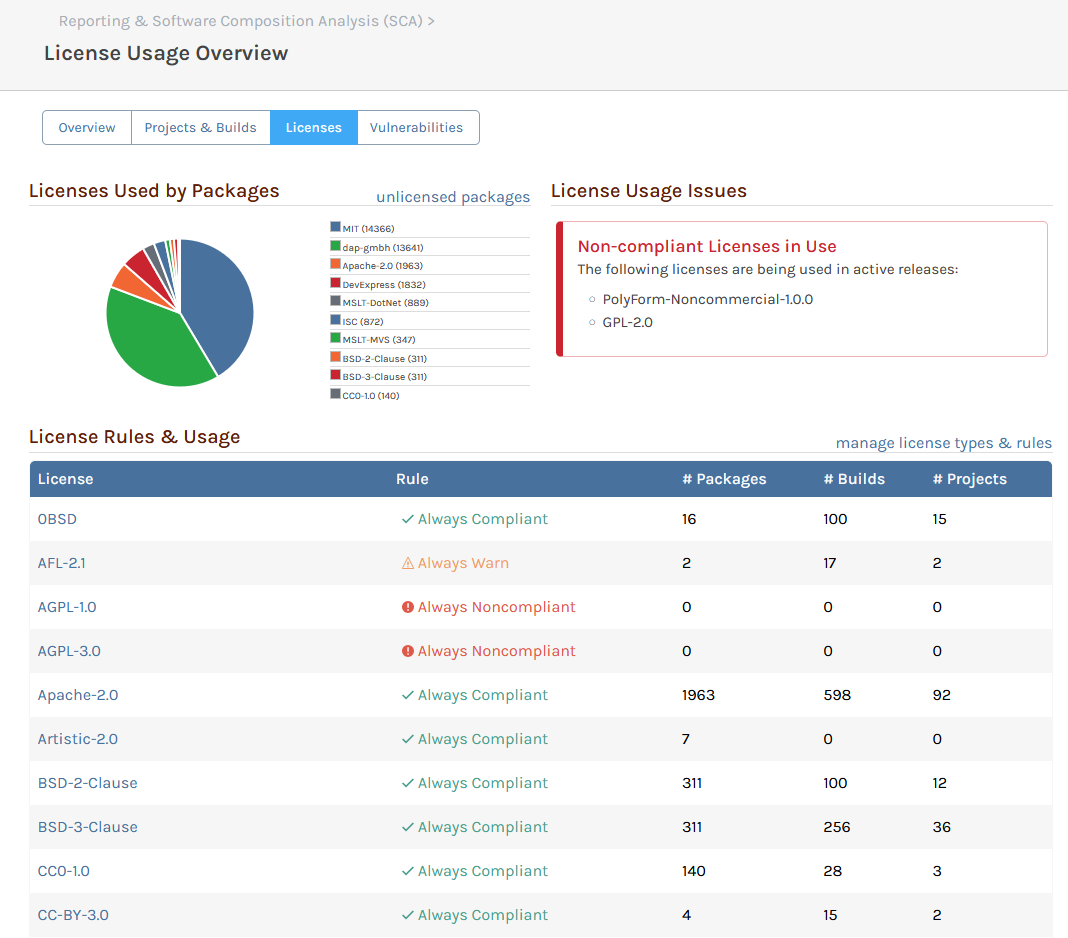
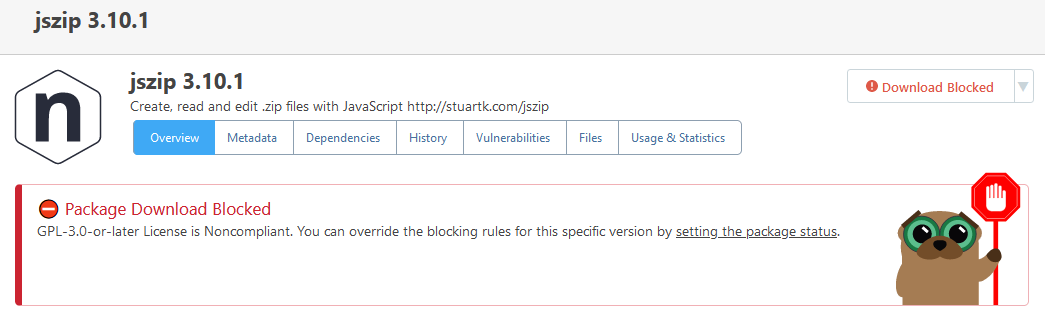
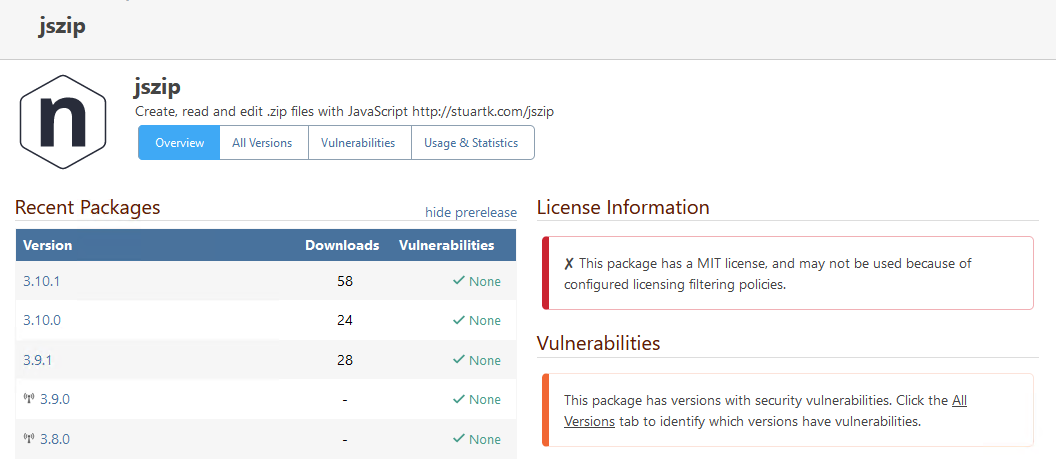
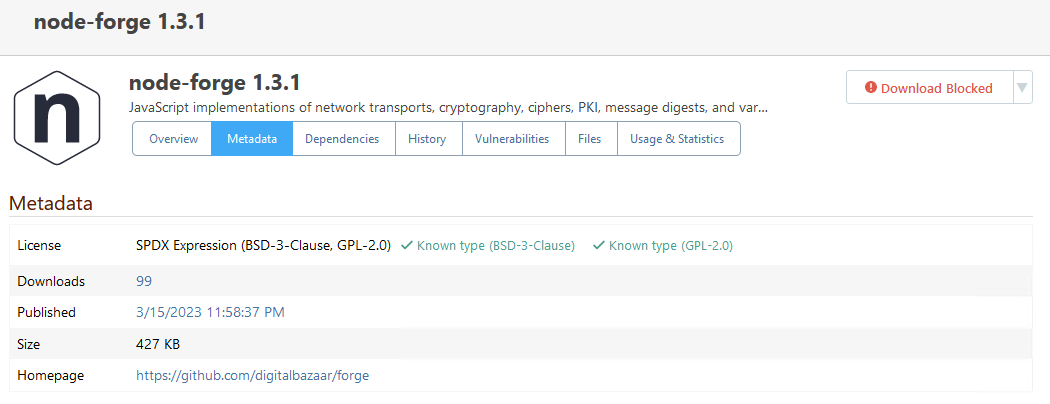
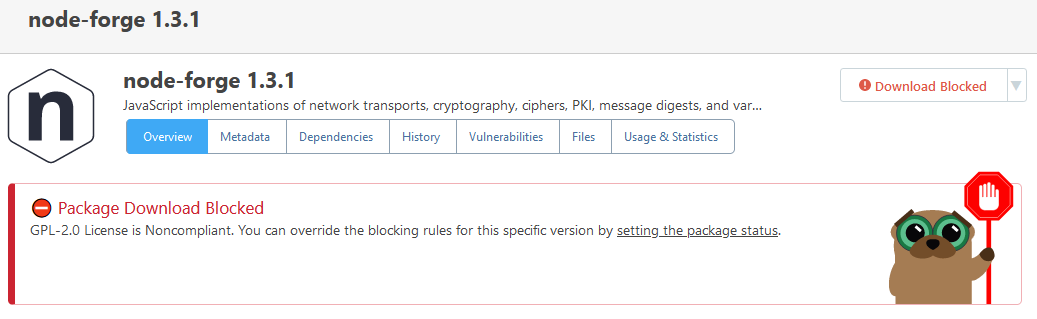
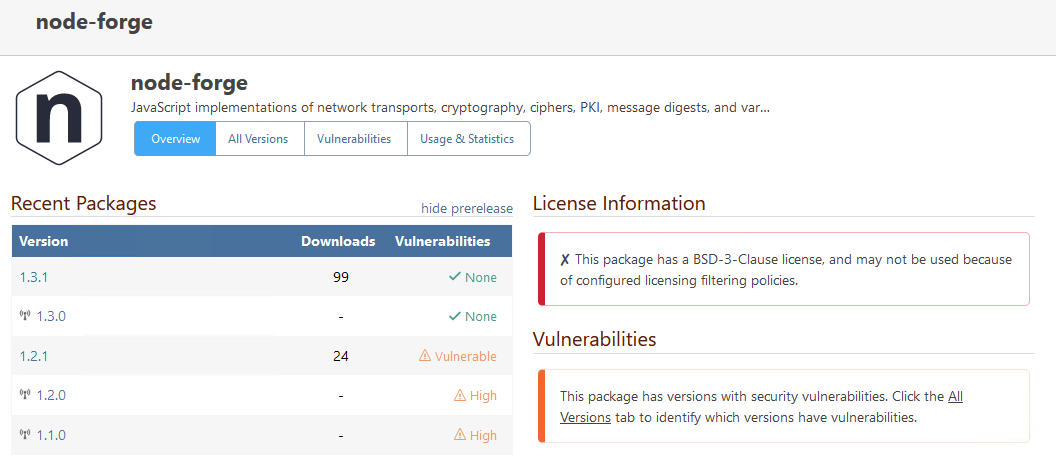
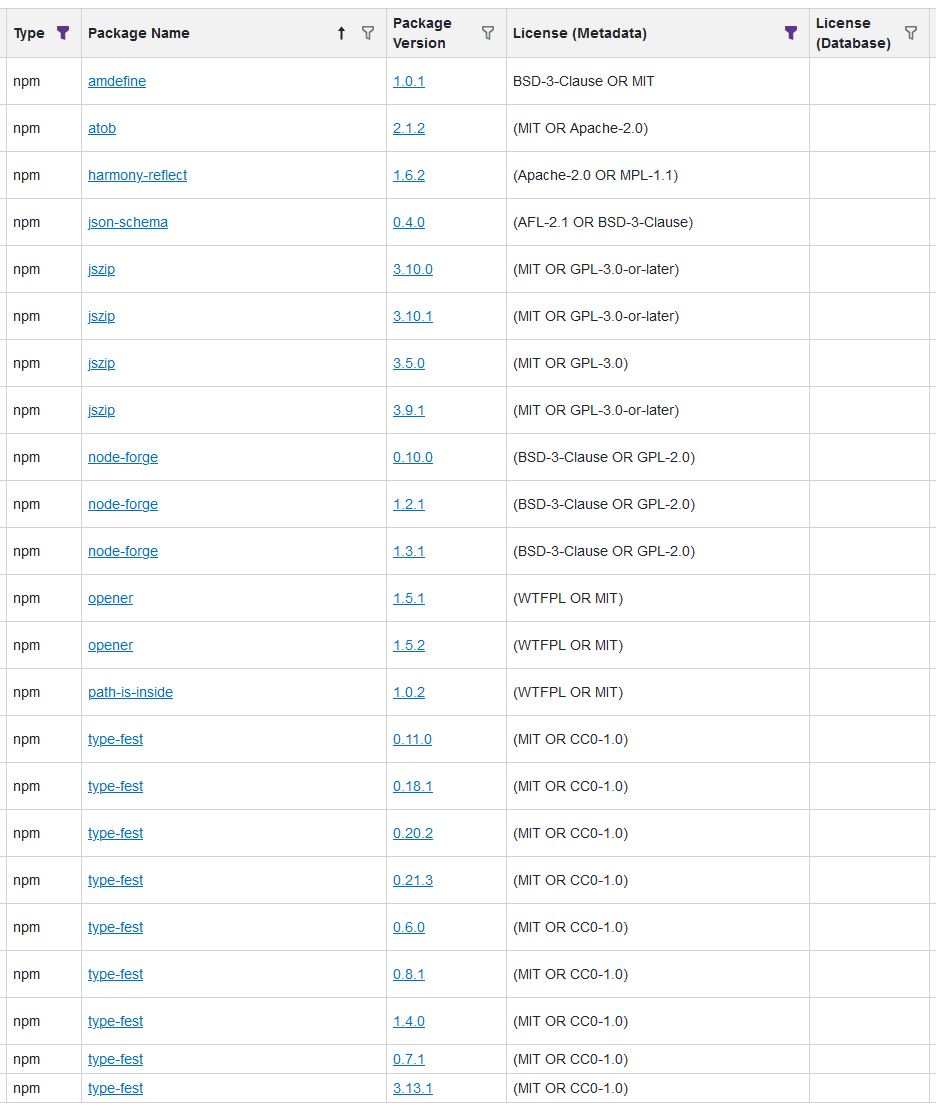
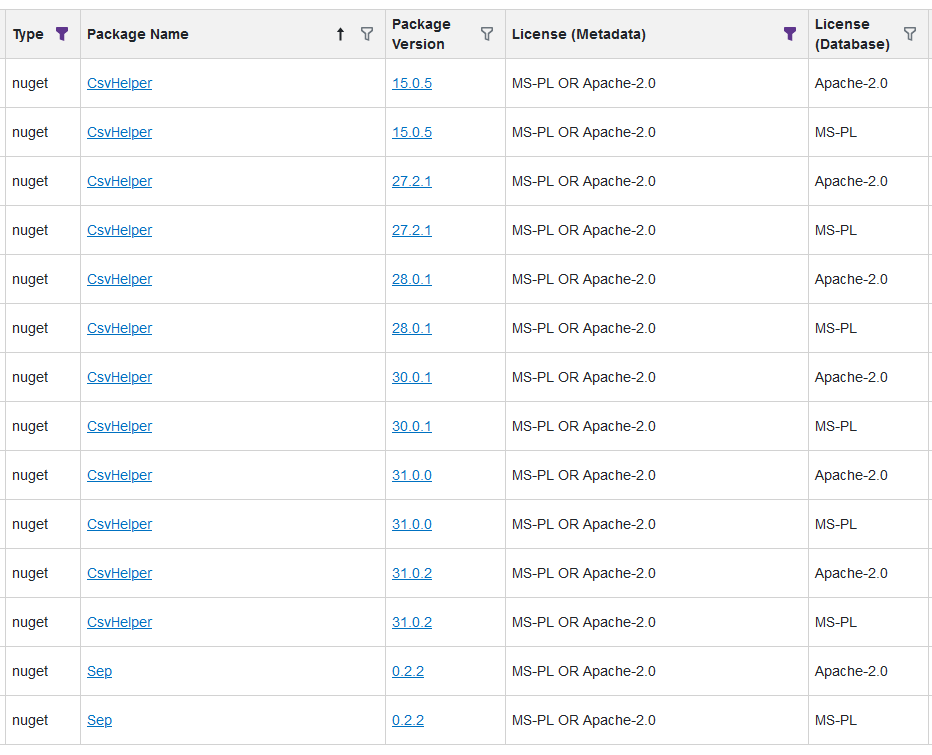
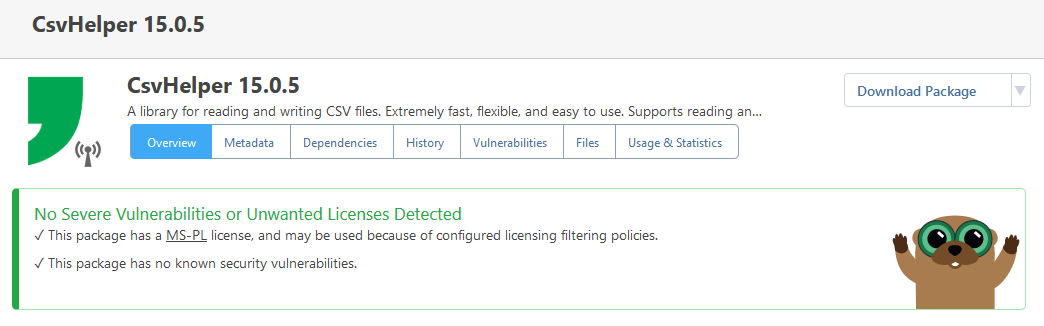
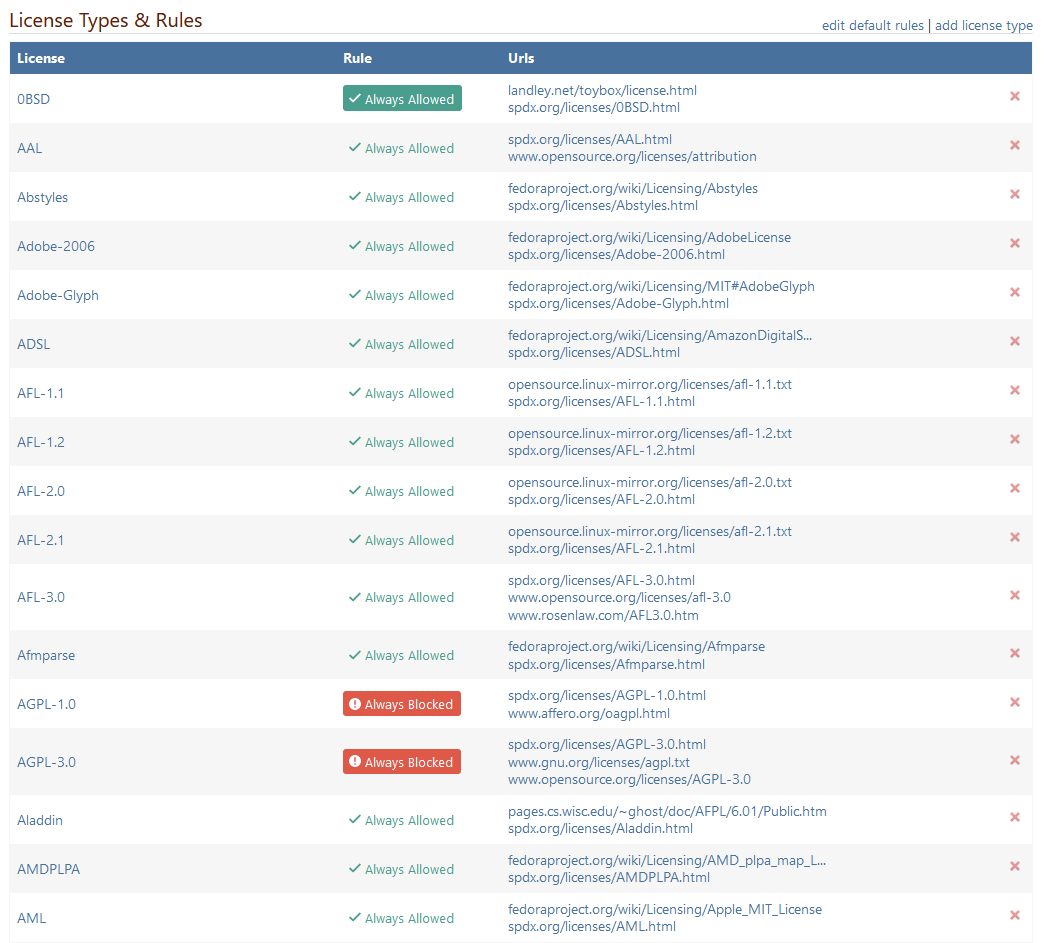
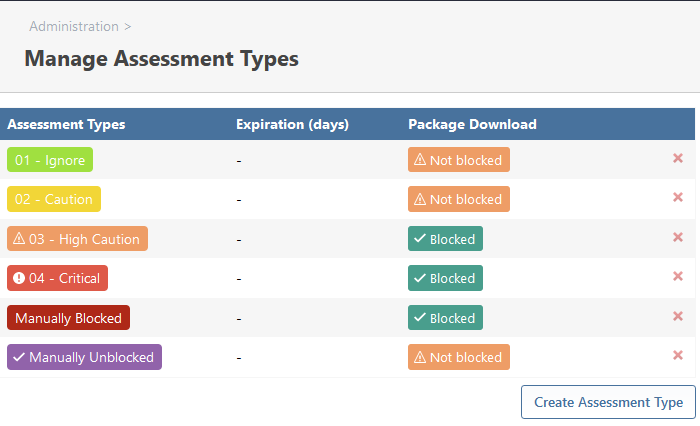
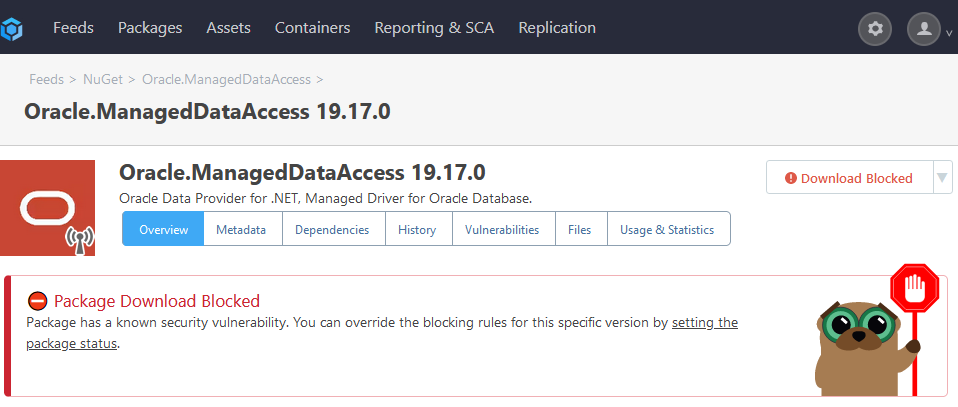
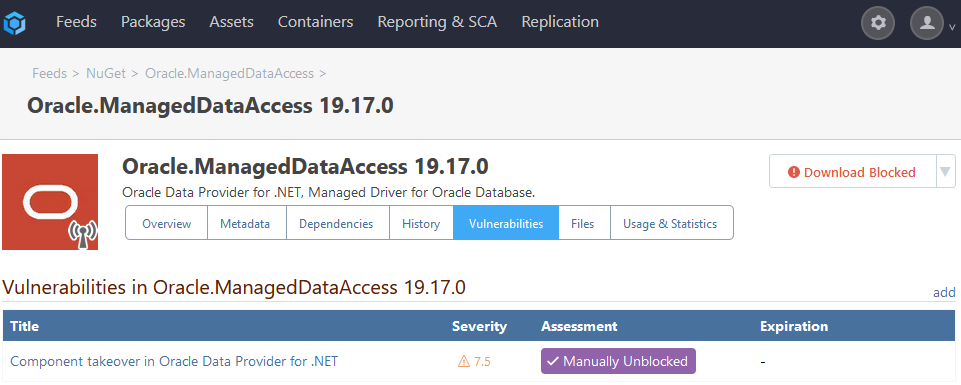
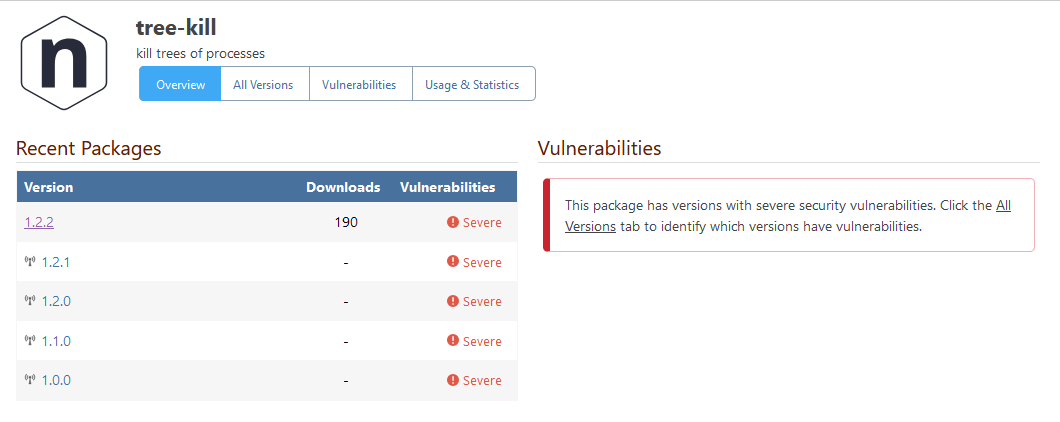
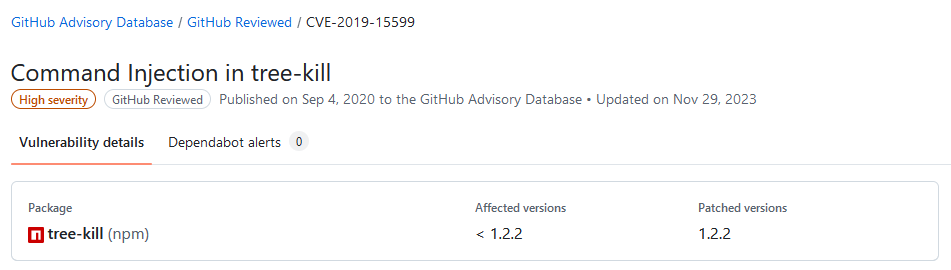
You are correct; it's not an urgent problem, because I can just choose a different assessment for that entry (we have a special assessment "Manually Unblocked" for cases like that). The other two entries are correct (i.e. they display the affected version as < 1.2.2 or <= 1.2.1).
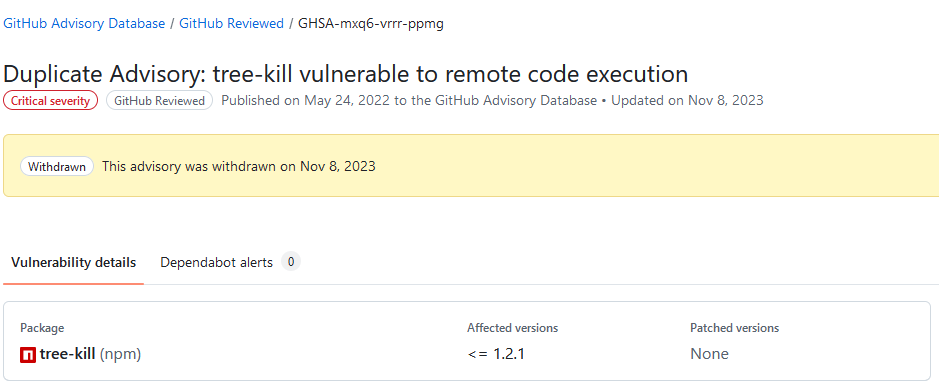
As for "Withdrawn" vulnerabilities... we're open to ideas for what to change in ProGet 2025. There used to just be a handful, but there are a lot more now. Our original was to just delete them from ProGet, but instead we just showed the icon. Maybe we should delete them.
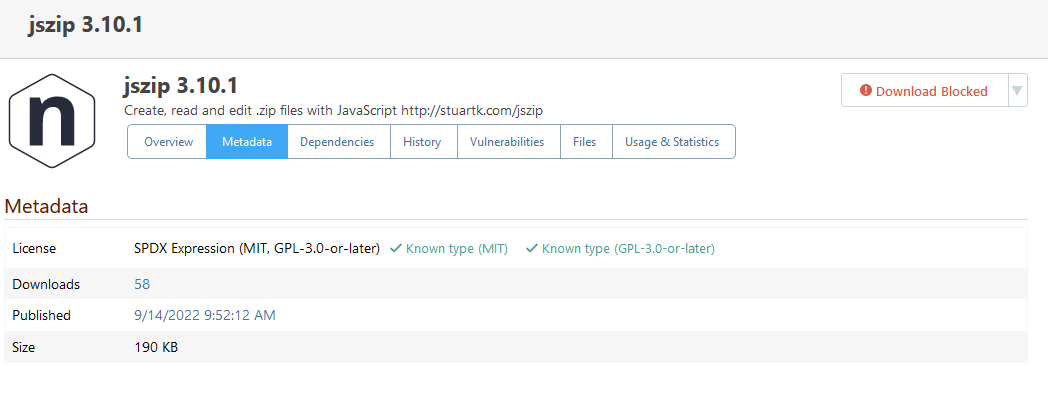
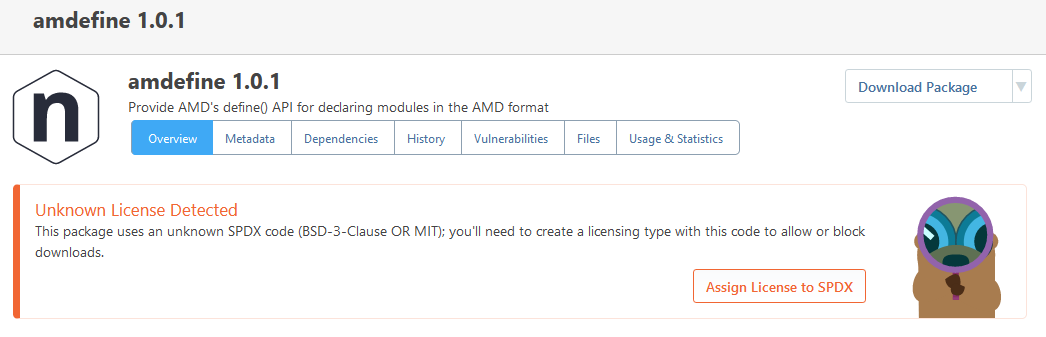
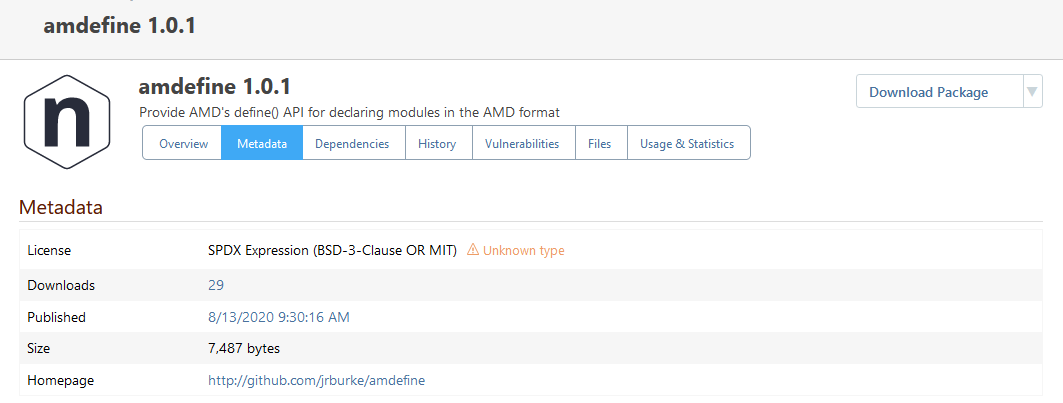
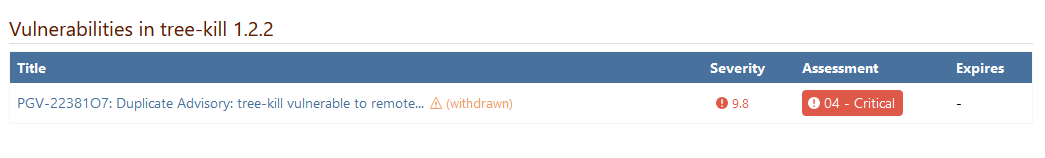
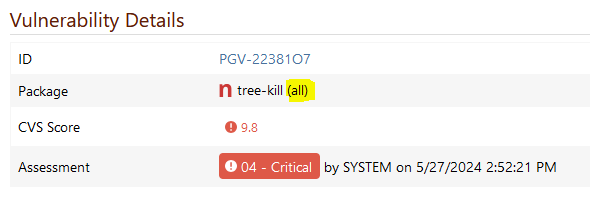
My guess is that PGV-22381O7 wasn't updated after it was withdrawn, so when version 1.2.2 of the package was released (and GHSA-mxq6-vrrr-ppmg updated "affected versions" to <= 1.2.1; again, I'm just guessing that that's what happened), the PGV entry didn't really reflect that.
It would expect one of the following two things to happen with withdrawn vulnerabilities:
-
The team at Inedo Security Labs should update withdrawn packages, especially when they flag "all" versions of a package as vulnerable.
-
There should be a special treatment for withdrawn vulnerabilities within ProGet. Maybe not deleting them (because I'm pretty sure there will be cases where I will be looking at a package and think "I swear this one had a vulnerability, but now I can't find it?"
 ), but maybe auto-assess a special status to it.
), but maybe auto-assess a special status to it.

 ).
).