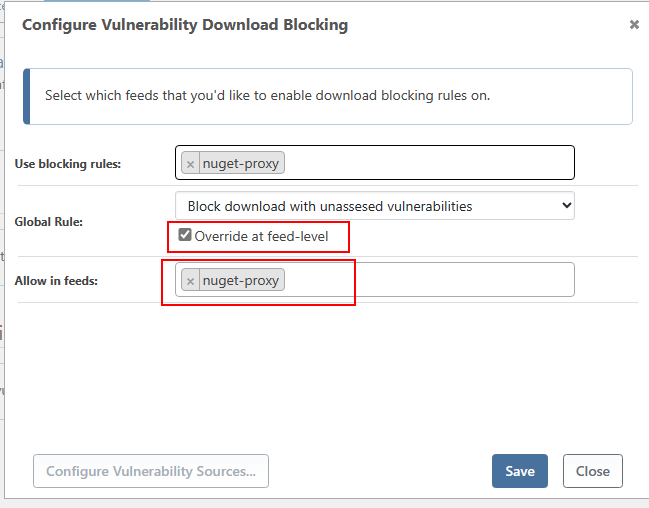
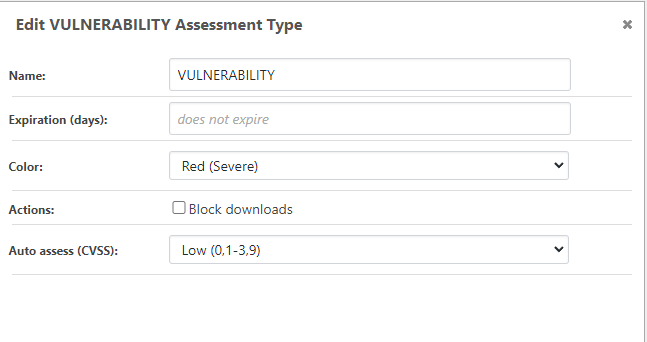
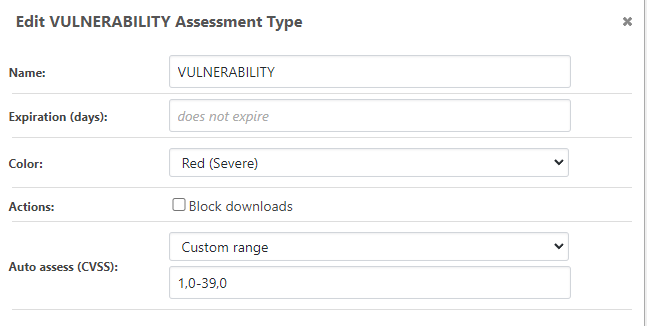
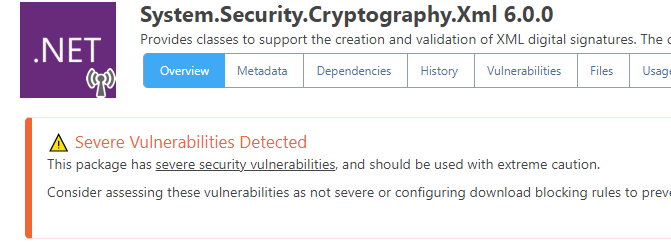
Obviously it's pretty easy to just wire up values (and we'd be happy to do that), but my only hesitation is documentation and cross-platform compatibility.
Cross-platform should not be an issue, since this is one of the reasons Microsoft created Kestrel in the first place. Of course the Windows cert store part of the configuration does not make sense in a Linux context, but that should be pretty much the only limitation.
Brainstorming a bit but... from the UI, we will just support one URL I think. I don't know why you'd want multiple...
From what I understand at least two URLs are needed to support HTTP and HTTPS side by side, but that could be abstracted away by the UI.
The docs you linked from Microsoft are confusing, and it's not really clear what fields to use or why. I guess, in general, you'd select a file (which InedoHub would generate?) or the cert store (that's Windows only, right?).
There are basically four sections that are of interest:
"Http" => Plain HTTP (Similar to Urls but just one host per endpoint)
"HttpsInlineCertFile" => PFX file based (Most likely be used by Windows users that don't want to deal with the cert store)
"HttpsInlineCertAndKeyFile" => .crt+pem file based (Most likely used by Linux users)
"HttpsInlineCertStore" => Windows cert store integration, only works on Windows.
I think the other parts can be ignored.
And I guess what, when you generate a cert yourself, it's a pfx or something? I always forget the differences....
PFX is just one possible certificate format, it is possible to generate all types of self-signed certificates. I believe the majority of business/enterprise users will probably use a cert they get from their IT department from the company-wide PKI and then they just need different options to plug that into ProGet.
Letting the user installing ProGet generate a certificate can be done, but it will show up as insecure (red, broken lock, etc.) in all browsers and also package managers will probably complain about it being untrusted. So I'm not 100% sure that implementing this time well spent, since there are a million guides on the internet how to generate a cert.
How would you suggest we modify that element to support the different options they have?
I would probably switch from the Urls parameter to a list of endpoints. This way the HTTP+HTTPS scenario can be supported as well as the the 4 options above.
The JSON from the example could simply be translated to XML 1:1.
<WebServer Enabled="true/false">
<Kestrel>
<Endpoint>
<HttpsInlineCertStore>
<Url>https://192.168.0.1:443</Url>
<Certificate>
<Subject>my.company.domain.local</Subject>
<Store>My</Store>
<Location>LocalMachine</Location
<AllowInvalid>false</AllowInvalid>
</Certificate>
</HttpsInlineCertStore>
</Endpoint>
</Kestrel>
</WebServer>
It should be possible, using the Microsoft.Extensions.Configuration.Xml, to read the config file into an IConfiguration object and feed the relevant portion into Kestrel, this is pretty much what we currently do. This way we don't have to reinvent the wheel with HTTPS configuration and can offer all the flexibility that Kestrel offers right out of the box.
new HostBuilder()
.ConfigureWebHostDefaults(webBuilder => webBuilder
.UseConfiguration(configuration)
.UseKestrel((context, serverOptions) =>
{
serverOptions.Configure(context.Configuration.GetSection("Kestrel"));
})