Hey, I have a bit of an odd corporate setup. I don't know the specifics, but we have some Entra hybrid sync thing going on that synchronises Entra cloud groups into local Active Directory. I'm pretty sure this is a standard offering from Microsoft.
I am trying to utilise this along with Entra Access Packages so that people can request access to groups and have them approved without needing go through an Active Directory admin.
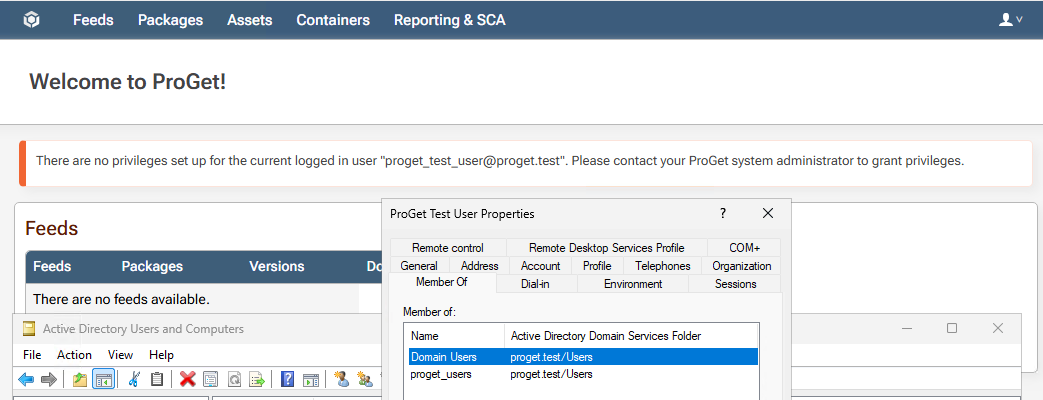
For login we use SAML SSO via Entra, not Windows Authentication. This is documented as ignoring group claims and going straight to AD.
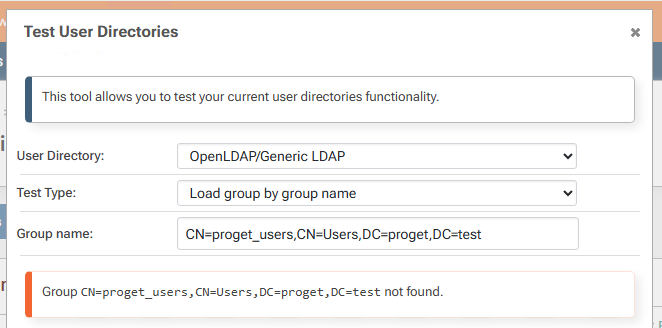
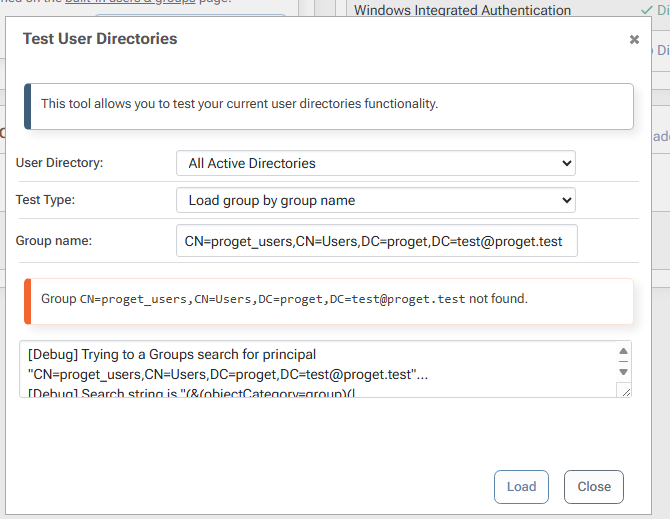
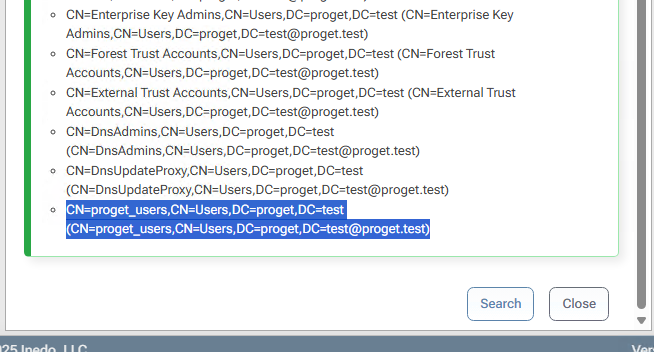
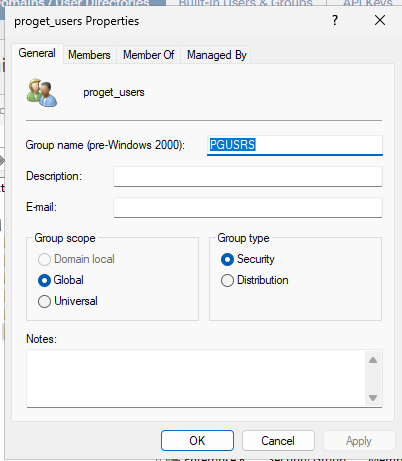
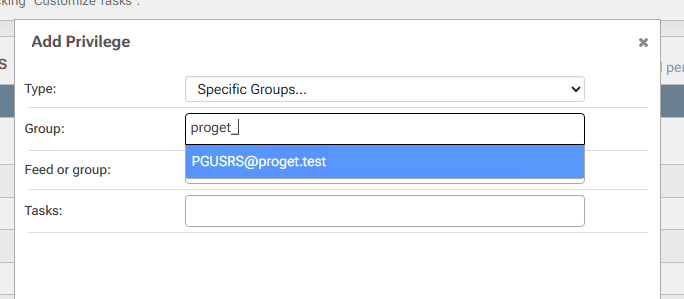
The generated AD groups have very odd names. They look something like $JQA200-TQZJ4H3I77X8@domain even though they have a long name of CN=cg_actual_name_plusrandomizedprefix,OU=Cloud,DC=domain.
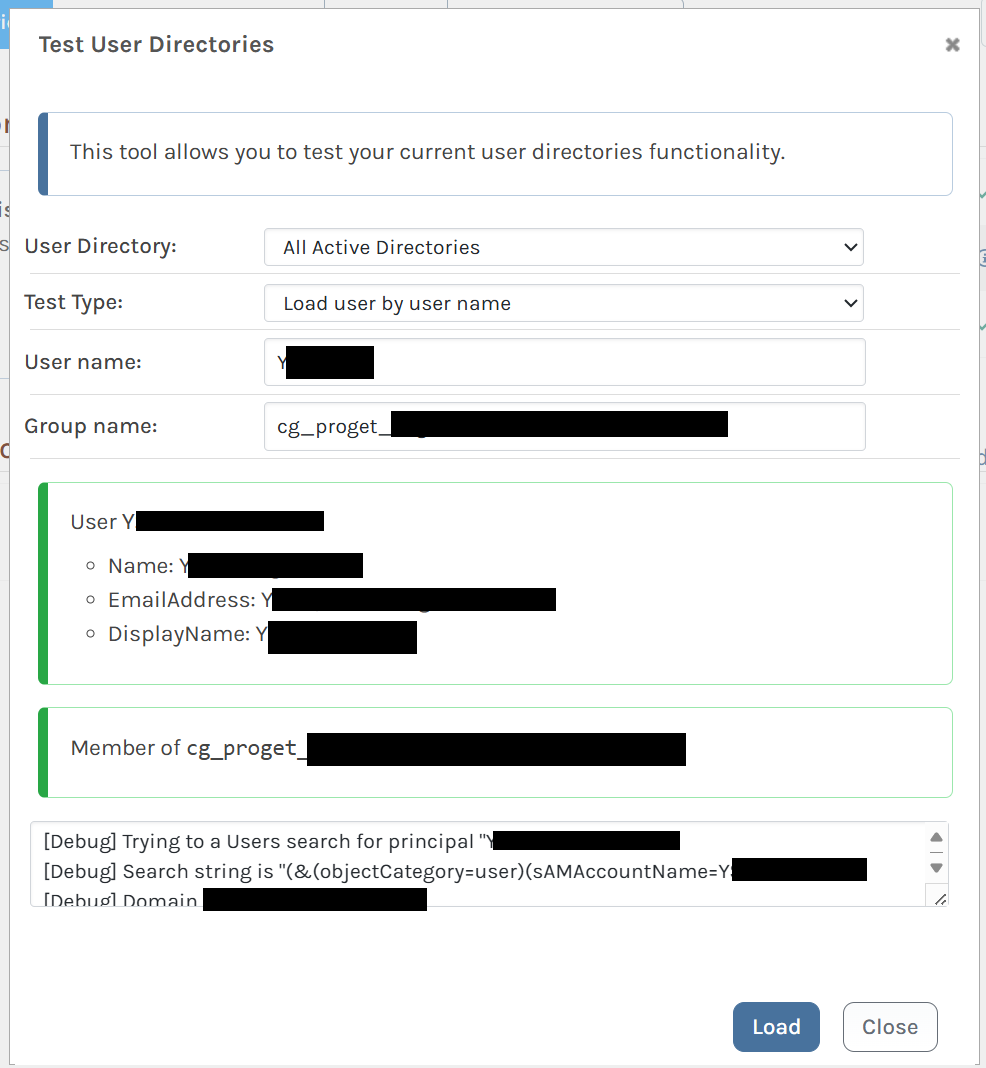
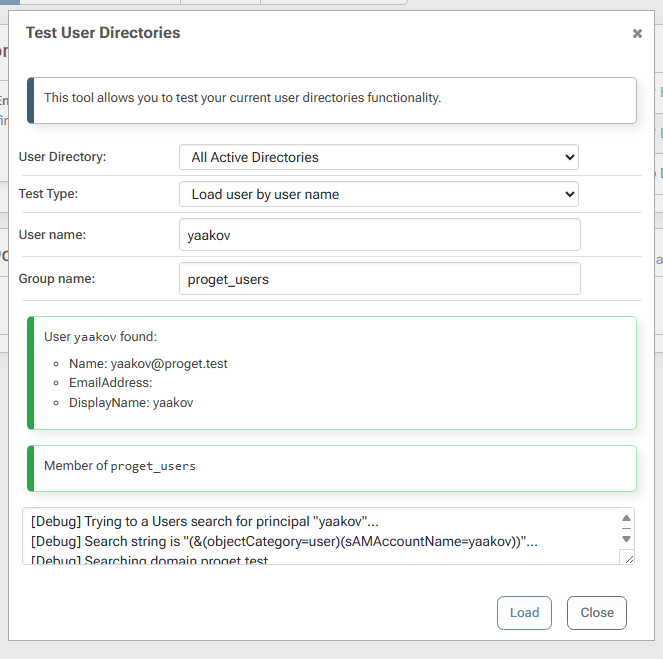
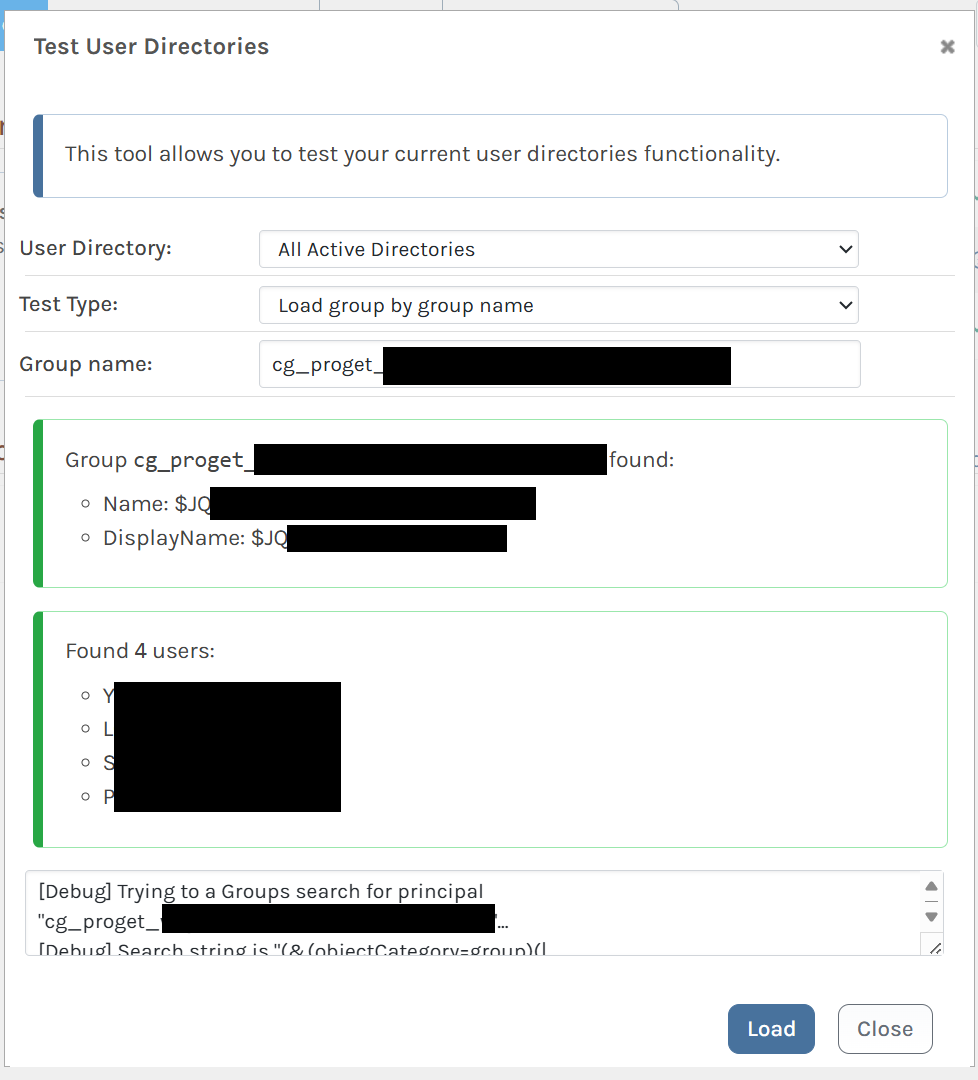
Using the "Test User Directories" feature of ProGet, I can see the members of the group whether I look up $JQA200-TQZJ4H3I77X8 or look up cg_actual_name_plusrandomizedsuffix, I can correctly see the members.
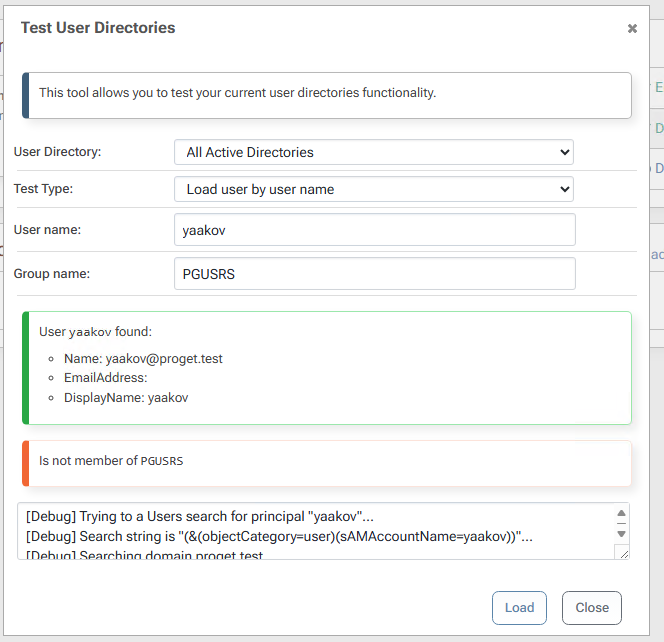
If I look up a user and group together, ProGet can see that a user is a member of cg_actual_name_plusrandomizedsuffix, but it cannot see that the user is a member of $JQA200-TQZJ4H3I77X8.
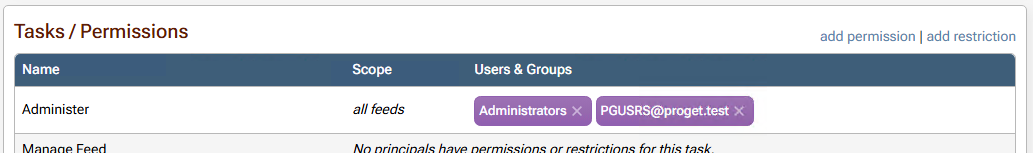
I believe this is the source of the actual issue I am seeing - when I assign Task permissions to $JQA200-TQZJ4H3I77X8 (e.g. Administer), users who are members of that group do not actually get those permissions.
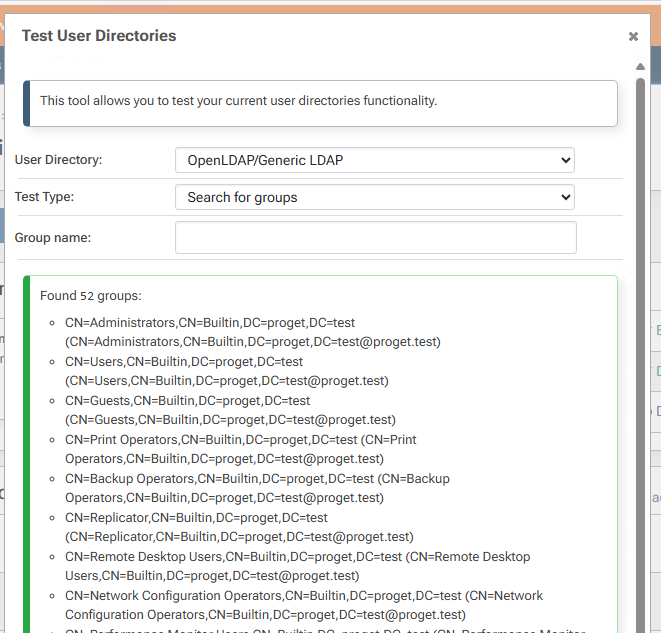
Group search:
Check membership by SAMAccountName
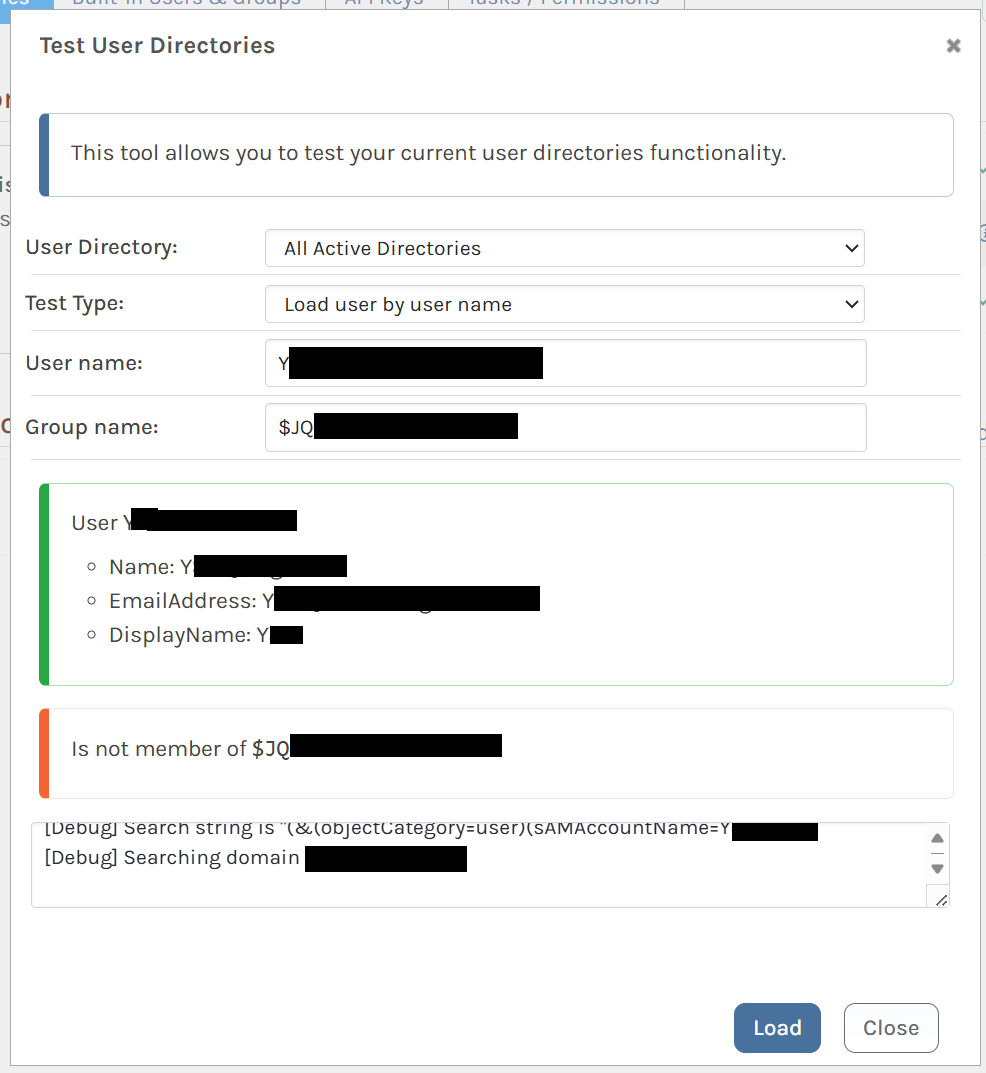
Check membership by Entra name (plus suffix)