Hi @apxltd
Your description sounds perfect. Look forward to seeing this in a future version.
Also your software products rock! Keep up the great work!
Thanks
Simon
Hi @apxltd
Your description sounds perfect. Look forward to seeing this in a future version.
Also your software products rock! Keep up the great work!
Thanks
Simon
Hi @atripp
I like your "tags that use this layer" suggestion, I was also thinking you could do something like this mock-up within the repo view:
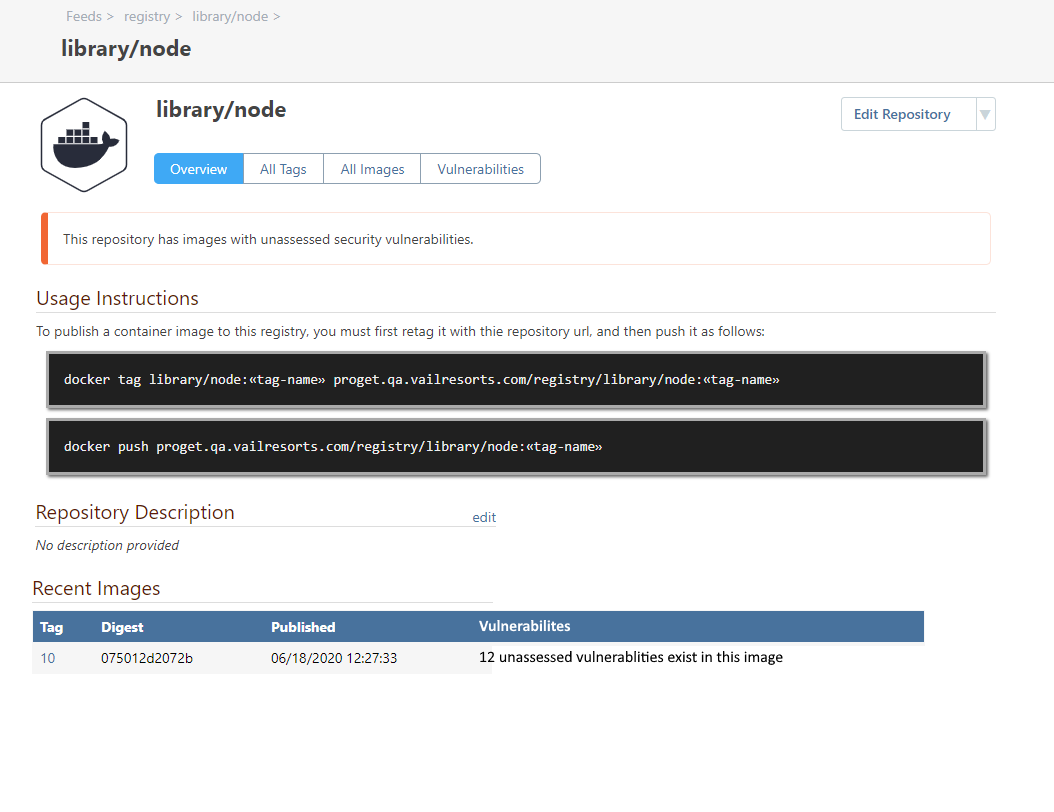
In addition you could also improve the "feed view" with some more information about the number of tags/images & vulnerablities per repo like this:
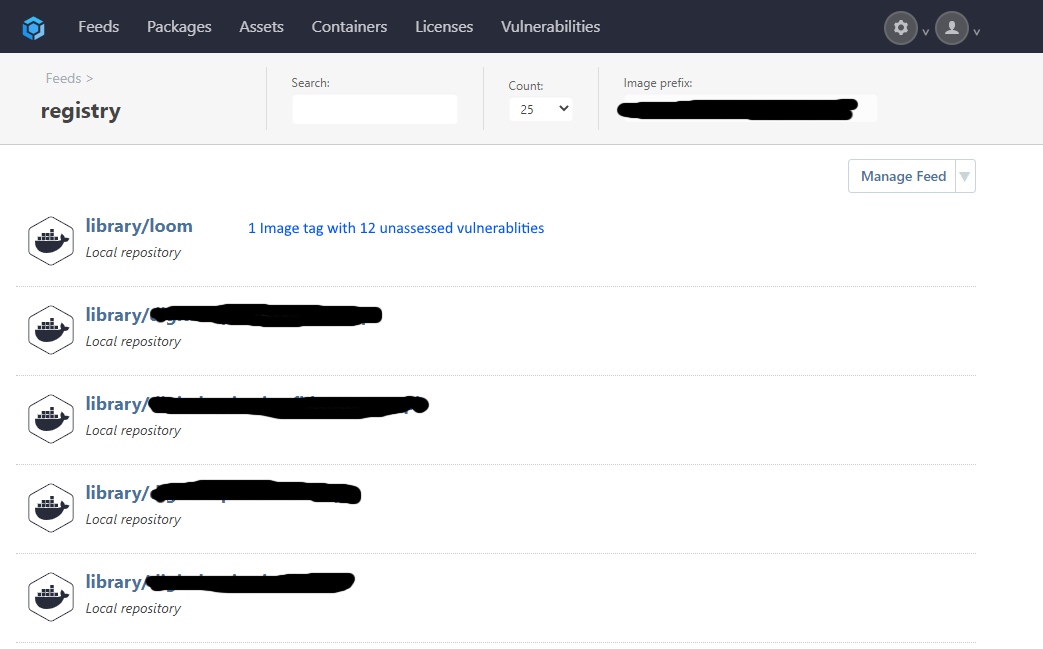
Or even:
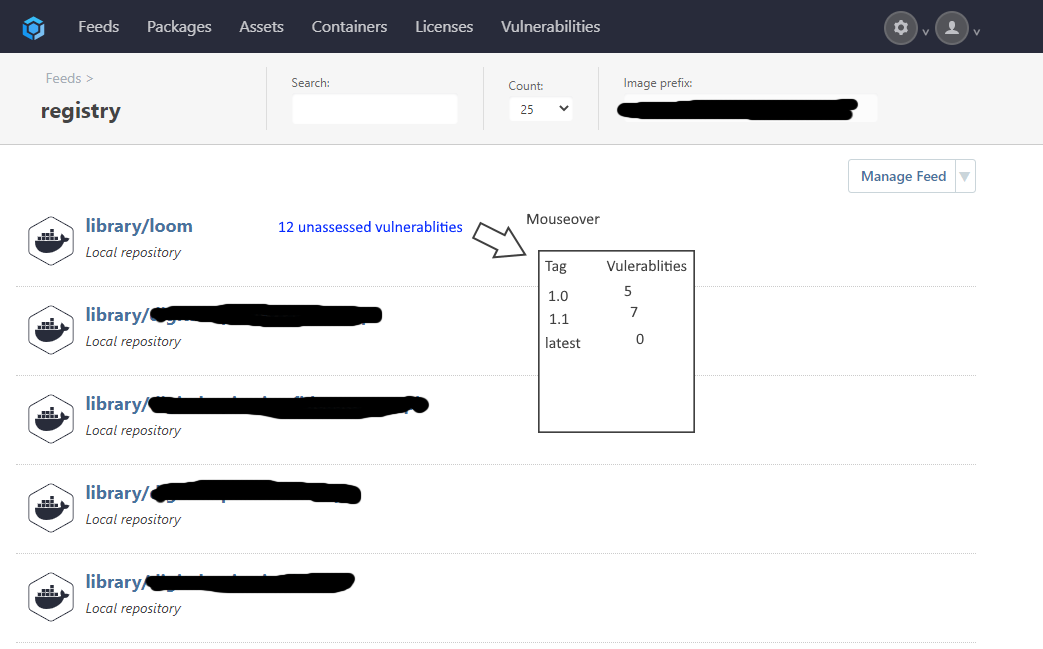
Hey Guys,
Hoping to submit a feature request here.
In Proget you should provide the ability for a user to manage their own API keys via the web interface.
At the minute API keys need to be setup by an administrator and assigned to a user via the impersonate user field.
It would be nice if the user was able to create their own API key via the user menu here:
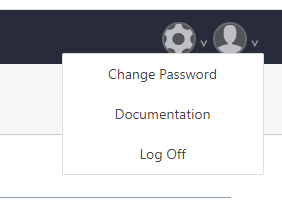
Use case:
Access to proget is setup using AD authentication and assigning an AD group (not ad user) with the correct privilege's.
The user then needs an API key to use with CI/CD tools on the users workstation.
Today:
Administrator needs to login to admin portal, add the ad user with the correct "security", then generate an API key and "impersonate" the user that has just been setup.
Required state:
User logs into the web portal and generates their own key that inherits the users current permission set.
Thanks
Simon