Hi,
Great, thanks! Apologies for not able to describe the problem better.
Best regards,
Daniel
Hi,
Great, thanks! Apologies for not able to describe the problem better.
Best regards,
Daniel
Hi,
I understand that docker image history does not show layers per se, but layers are show in a way. It's correct that there are 24 layers and ProGet does show 24 rows. But the commands shown for some/most layers are wrong, it's as if it does not skip non-layer generating commands. There are several commands in our Dockerfile that sets environment variables for following RUN commands.
Here's part of command from Dockerfile that generates layer 24:
RUN /bin/sh -c : && tar -C /tmp -xf /tmp/...
And here's what ProGet show for layer 24:
RUN |2 proxy_host= proxy_port=8888 /bin/sh -c...
The command that ProGet show is used to generate a layer earlier in the Dockerfile.
Best regards,
Daniel
Manifest:
{
"schemaVersion": 2,
"mediaType": "application/vnd.docker.distribution.manifest.v2+json",
"config": {
"mediaType": "application/vnd.docker.container.image.v1+json",
"size": 14147,
"digest": "sha256:ab4eca7160c7cbb7ca656fc567ff13eed767066b4ea662ceea31b9ce8e44f2ad"
},
"layers": [
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 79078981,
"digest": "sha256:e60c9fe2676d1fc11442d4ccd62ed958bdeb07c2a637cbdc10e2eef235b66814"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 22354231,
"digest": "sha256:c061909f4a7a21b0ffe2c5fcc606ce8d0106b461ec7b1c2f414cdb50e061e2d3"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 3817,
"digest": "sha256:8de8dab7a9d012b3e23f5afa40b62627f2c263be798552b855b3a3630950cc3f"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 32,
"digest": "sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 4430,
"digest": "sha256:aa3ef9e322efe6117e81bc3d5e90858570d330d12bbb4d83f8bf494b97282634"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 21657612,
"digest": "sha256:ceeb0cf101bb99324b382ffa5bcf6c9d8b457f1c139e1ba29996366722a5711f"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 1379,
"digest": "sha256:bff29e0a6e38370cd786eb41e5b804651fc004d6981526e0ba2eb2ced51cff37"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 945288,
"digest": "sha256:5549a014dacbbe1fb9703b00faed6ce3e39b7c83bafaee5e13f56b24e38899e5"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 325129588,
"digest": "sha256:e594dc179bfc37e9c8c746b7c303651c5472dd6702f9aac03e4babdff540531e"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 32,
"digest": "sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 32,
"digest": "sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 1238929,
"digest": "sha256:6897a98c90464f6521787c0a5410533790d266c63c732afa860b2d5fab2720b2"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 16767228,
"digest": "sha256:d69ae6da49ed40a5c9cf51194ea5f4f7d18de50e85a0b9d4da276785cadd0626"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 8906037,
"digest": "sha256:982da0f0876345605ae557d61a92ee45399553bd0a5806b8c3e62548df32e002"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 130,
"digest": "sha256:d7a1da484429e49793b180eeef361b16534a7f7bbe4b00067fa0397bc1f92fad"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 4940215,
"digest": "sha256:4ee7dcf865d60d11363aa61338a4aa22116540d3b87ea087730419922c22e68e"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 16399337,
"digest": "sha256:4529bcd3ea1bf888fce1d9d7887243ce879e69408e65ce764a99860eef9ae68f"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 92,
"digest": "sha256:b33640e583ab6f826c3dcb7956be9a4cad8f9b1eb8c83594518b8fb67e6c5281"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 1842985,
"digest": "sha256:95c6edbc8b63924db8268f4b698fa82daa10af2d6d81020fc29c3a2ad7418222"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 11610611,
"digest": "sha256:f4340cf7e51f815647974cc1771b2dffa77e0f5eba4a57721bc05e9af6c6ad57"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 32,
"digest": "sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 25434,
"digest": "sha256:80d412a28329389087d676a767297becd692057d56043d1019af006c430fac7e"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 43891830,
"digest": "sha256:a6a36d1c2e9abece59b383c3f93c39d060a48ae4a9d3047408bc05aa09c9c5b1"
},
{
"mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip",
"size": 13829131,
"digest": "sha256:b7593e740f79fdea31249ff3717f4fe50dc1925ca728bb423e56e12e2e1b4b6e"
}
]
}
I could also provide the configuration JSON, but rather send that outside of forum.
// Daniel
Hi,
I understand that. But again, there are layers after what ProGet shows. Regardless if ProGet only shows layers or not, it's missing the latter layers from the image. There are about 7 or 8 after the last one from the screenshot.
Thank you for your patience,
Daniel
Hi,
Thanks for clarifying the differences.
But still, ProGet does not show the all information that docker image history shows, it's cut off two-thirds in. As you saw from above, there are 36 lines to the CLI output, but ProGet only shows the 24 first of those:
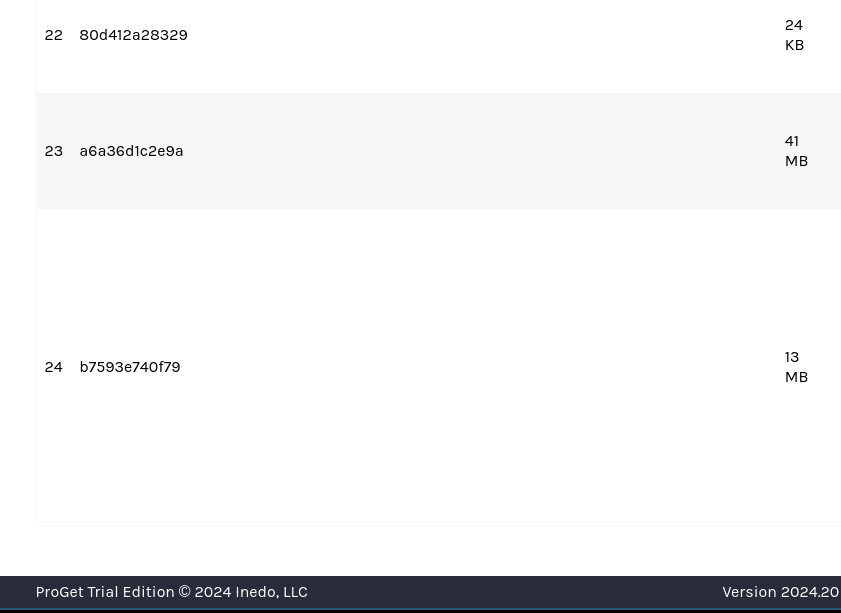
Best regards,
Daniel
Hi,
No, no custom extensions. Just some from https://proget.inedo.com/feeds/Extensions, such as Jenkins and Sonatype. It's not clear to me yet how they fit into ProGet or how they can be used.
From https://docs.inedo.com/docs/proget/administration/extensions:
You can see which extensions are loaded, as well as install new or update extensions from the Admin > Extensions Page from your instance of ProGet.
I could ever only install updates to already installed extension, not install new.
Best regards,
Daniel
Hi,
Yes, according to this (first line is a header):
% docker image history <image> | wc -l
37
Last layer shown in ProGet is the 24:th item according to above command. Perhaps layer is not the correct terminology but Layers in ProGet does not show all that docker image history shows.
Best regards,
Daniel
Hi,
Our images have quite a few layers. Up to about 36, but about 10 of them are just LABEL and ARG lines. When viewing the image in ProGet it only shows up to 24 layers. Is that intentional?
Best regards,
Daniel
Hi,
From my understanding it should be possible to install extensions from the Administration > Extensions page. I don't see any option to add new extension there, only to update existing ones. Is there a setting that must be enabled? If it matters this trial installation is running inside a Docker container on Debian stable.
Thanks in advance,
Daniel
Hi again,
It seems I can only request trial for Basic Edition. I would like to verify a few things that only exist in Enterprise Edition. How could I request and extension of that?
Thanks in advance,
Daniel
Hi,
Thanks for your response. And apologies for my delayed response, I got sidetracked with things for a while.
That Builds are tied to SBOM and only to other packages indirectly was the missing link for my understanding. Thanks.
Besides proxying public repositories for Debian, CentOS, npm and maven we want to have one authoritative place that knows what builds/releases are made up of, and potentially download them from. This is where feeds/connectors and SBOM/SCA come in. I believe feeds/connectors will work fine, I still have some more tests to do there.
For the products I'm working with I don't think pgutil scan will work out of the box. We would be fine with finding solutions to create/manage SBOM ourselves, if it means we can still use the rest of the functionality.
Regarding which problems we're trying to solve:
Given my new understanding on how ProGet operates I believe it would work for us, but there are still a few thing I would to verify. Our trial license expire while I was tied up with other things, would it be possible to get an extension to that?
Hi,
I'm currently evaluating ProGet and have some questions.
The product I'm working with does not generate packages as such during its build. Rather various archives that contain installation scripts or add-on products that are managed by the base product. I suppose these would be Assets in your terminology. From my understanding Builds can only contain proper packages? And not Assets?
Given above I suppose we could package our artifacts as Universal Packages. I've done that for one artifact but it's not clear how I can add that package to a build. I tried using the web UI but I don't know what "purl" is supposed to look like. Do you have any information about that?
If Universal Package is the way to go, how can I add that during the build with "pgutil"? It seems "pgutil" can only scan for dependencies, and can't see how it would pickup our Universal Packages.
Would SCA be able to scan our Universal Package? It's an archive containing RPMs (among other files) that is to be installed on a server.
From our Universal Package can ProGet detect/correlate dependencies from feeds/connectors?
Thanks in advance.