Welcome to the Inedo Forums! Check out the Forums Guide for help getting started.
If you are experiencing any issues with the forum software, please visit the Contact Form on our website and let us know!
Proget Duplicate Vulnerability for NPM Package
-
I noticed that we have two vulnerabilities for the same CWE-400 issue that have different ID's:
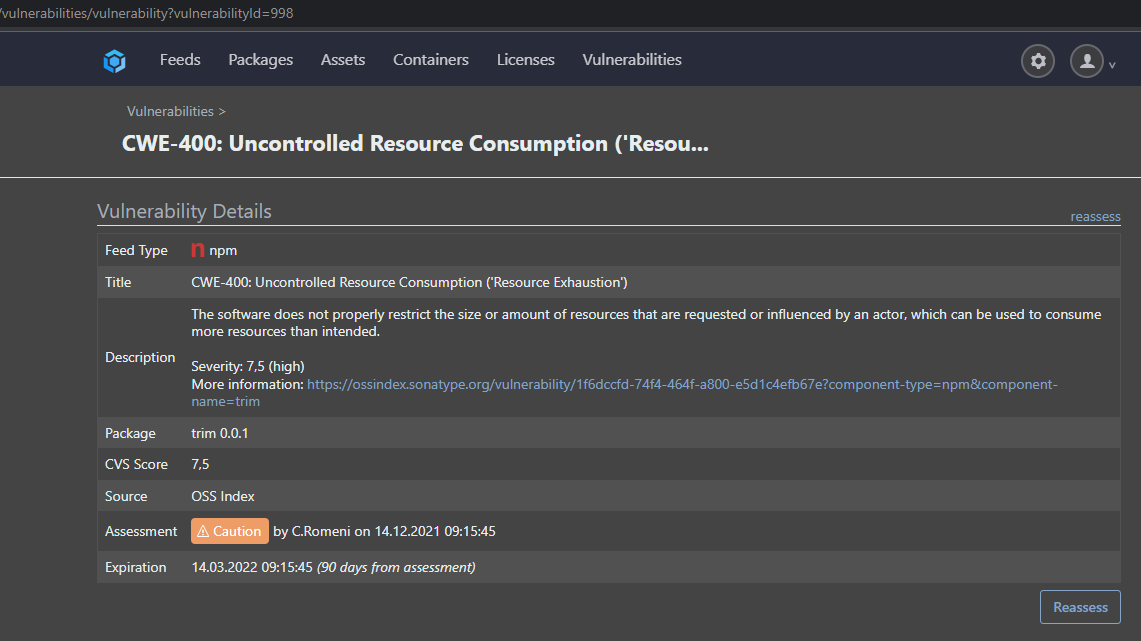
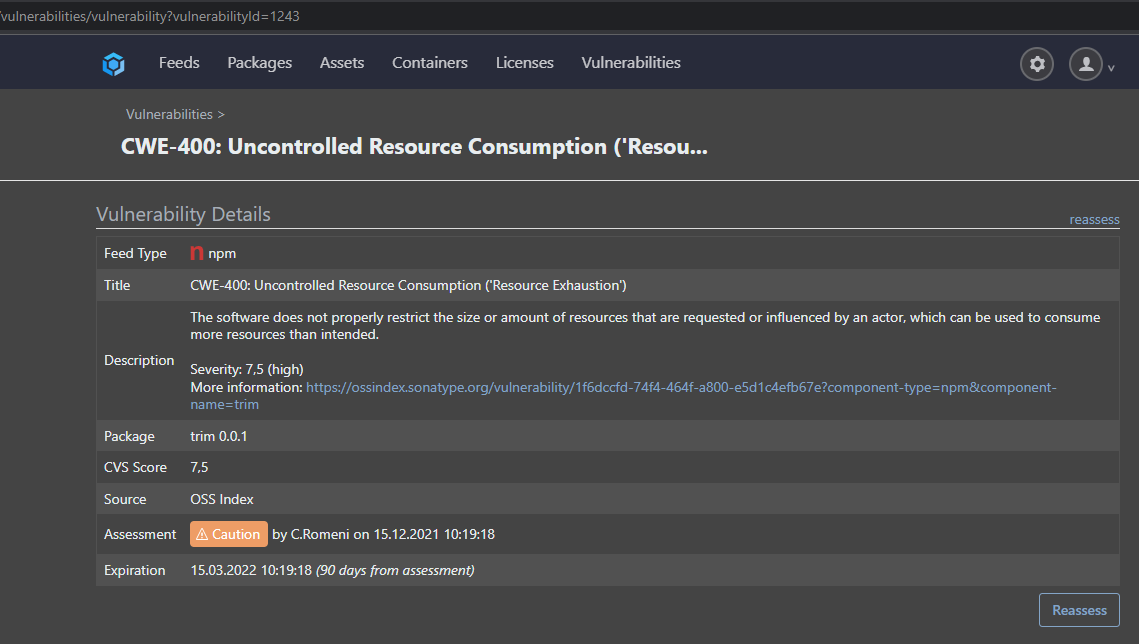
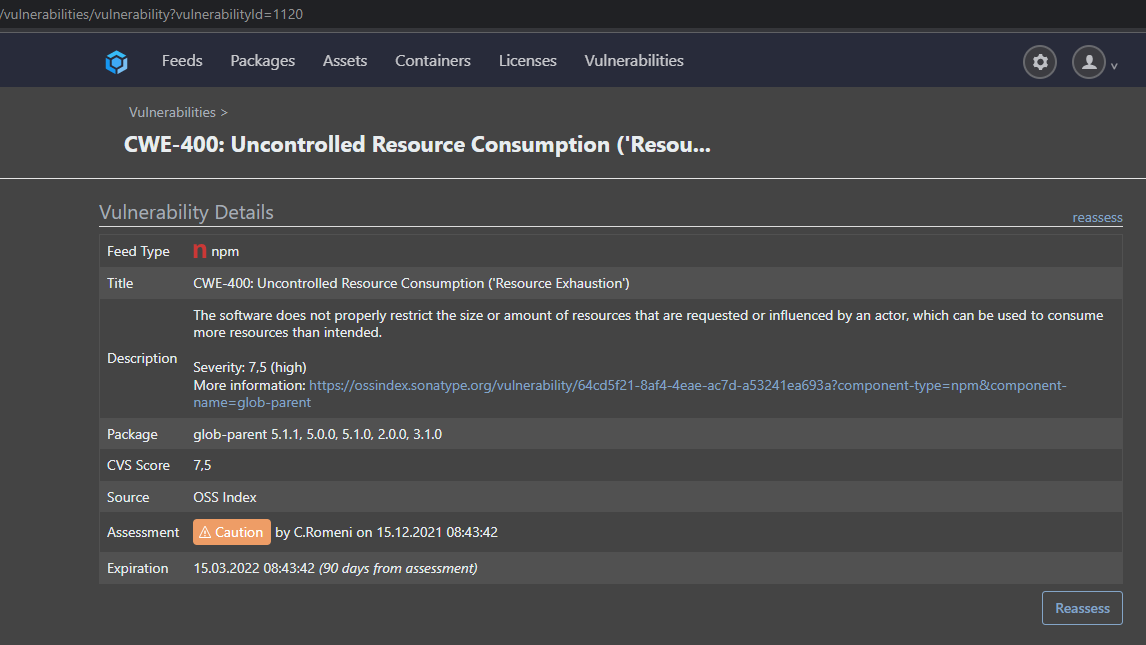
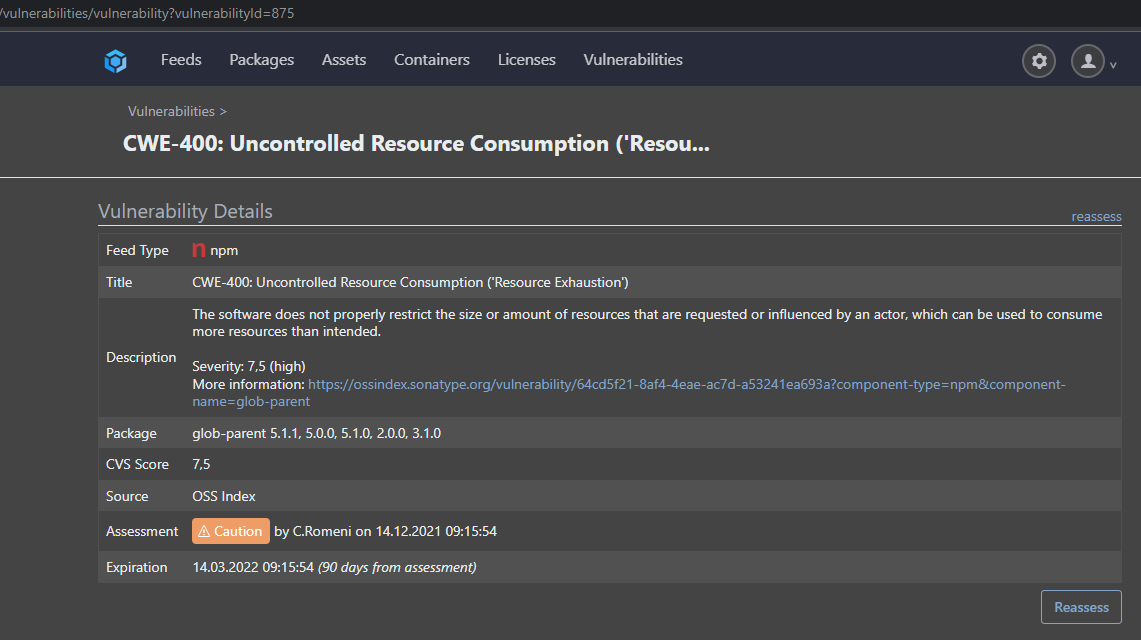
xxx.xx/vulnerabilities/vulnerability?vulnerabilityId=875
xxx.xx/vulnerabilities/vulnerability?vulnerabilityId=1120They are both completely equal (at least it looks like it). The only difference, one was already marked as "Caution", the other was new an unassessed.
This lead to npm installation error, since we dont allow unassessed vulnerabilities.
We are running ProGet 6.0.4 (Build 8).
Any Ideas why this happened and how we can prevent the same vulnerability to appear twice with different ID's?
-
Hi @cronventis,
Do you have multiple vulnerability sources configured in your ProGet instance? Are you able to provide screenshots of the actual vulnerabilities in ProGet?
Thanks,
Rich
-
We have OSS and Clair, so yes, we have two.. But Clair is not used for npm..
1a.
1b.
2a.
2b.
-
And today I got another one:
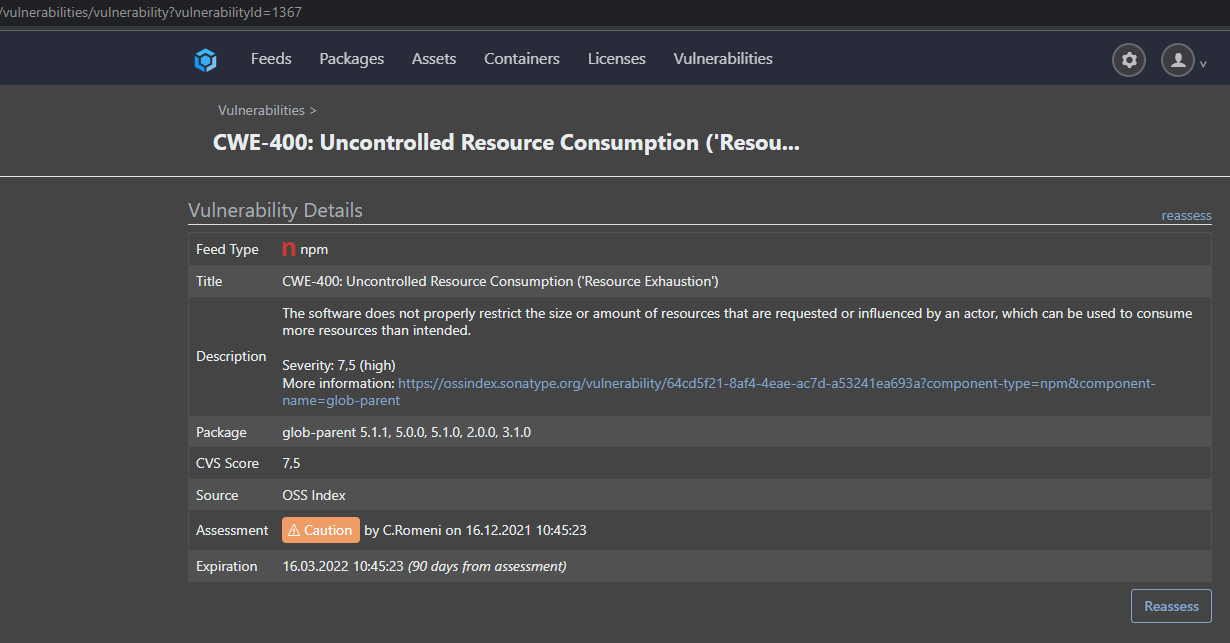
And as you can see, its always the same issue
Since the Update to Version 6 was done on saturday last week (5 days) and we currently have 6 times the same issue, I would actually think its a daily task the duplicates the vulnerability (+ the original that has been assesed before the update)
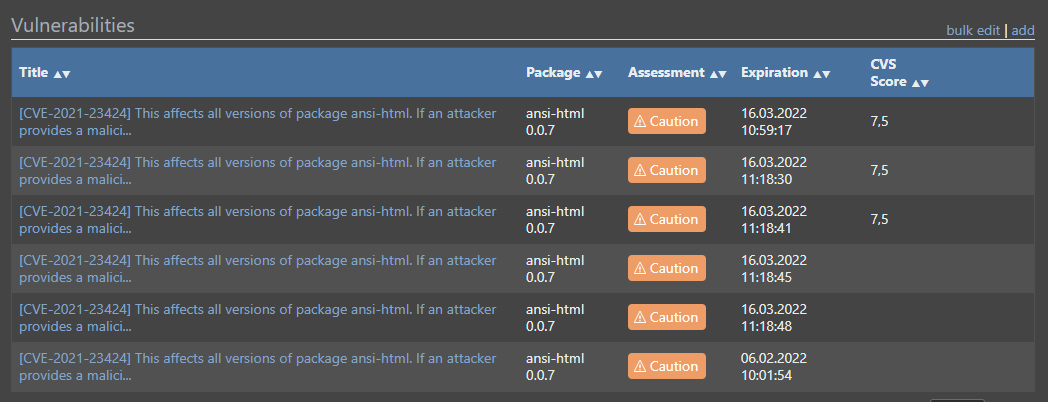
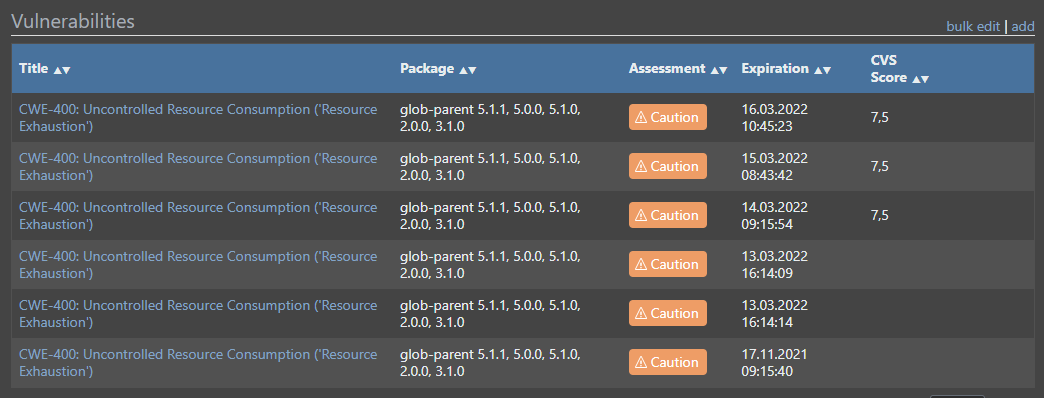
-
Hi @cronventis,
Thanks for sending this over. I have found the issue, PG-2064, and have fixed it. It will be released tomorrow in ProGet 6.0.5.
Thanks,
Rich
-
Awesome.. Will the duplicates be removed automatically?
-
Hi @cronventis,
The fix will only prevent new duplicates from being created. Mainly this is because I cannot ensure that the first vulnerability is always the properly assessed vulnerability. For now, the best option will be to run a SQL query directly against SQL Server ProGet database after you upgrade to 6.0.5.
I have created a SQL query that will delete all the duplicates excluding the first vulnerability that was added to ProGet. If that criteria works for you, this query should be good enough.
BEGIN TRANSACTION DELETE FROM [Vulnerabilities] WHERE [Vulnerability_Id] in ( SELECT v.[Vulnerability_Id] FROM [Vulnerabilities] v INNER JOIN ( SELECT [External_Id] ,[FeedType_Name] ,[VulnerabilitySource_Id] ,COUNT([External_Id]) as [NumberOfDuplicates] ,MIN([Vulnerability_Id]) as [FirstVulnerability] ,MAX([Vulnerability_Id]) as [LastVulnerability] FROM [Vulnerabilities_Extended] GROUP BY External_Id, FeedType_Name, VulnerabilitySource_Id HAVING count(External_Id) > 1 ) duplicates on v.External_Id = duplicates.External_Id WHERE v.Vulnerability_Id != duplicates.[FirstVulnerability] ) ROLLBACKCurrently, I have the script set to rollback at the end (meaning it won't actually delete the duplicates). If this works for you, you can simply change
ROLLBACKtoCOMMITand rerun the query and it will remove the duplicates.Please let me know if you have any questions!
Thanks,
Rich