Welcome to the Inedo Forums! Check out the Forums Guide for help getting started.
If you are experiencing any issues with the forum software, please visit the Contact Form on our website and let us know!
Vulnerability checking on Maven packages
-
Currently running Version 2025.17 (Build 20) of ProGet.
Do we have something configured wrong, or does the vulnerability checking not work well for maven packages and the weird version sorting that these use?
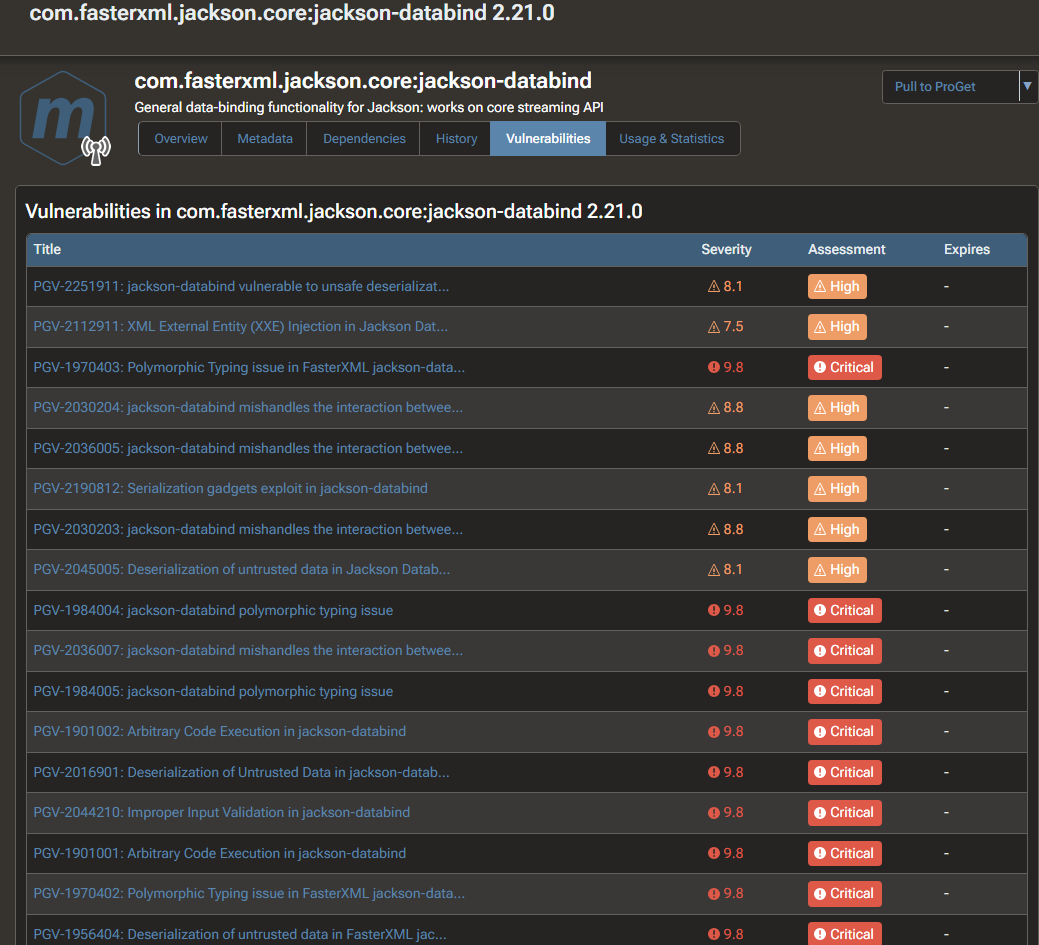
For example, if I look at version 2.21.0 for com.fasterxml.jackson.core:jackson-databind, it shows a huge list of vulnerabilities for this version, but the vulnerability details show that these vulnerabilities are for versions that are older than 2.21.0.
2.21.0 doesn't seem to have any vulnerabilities itself, but due to the version sorting it seems to be getting associated with lots of old vulnerabilities.
Is there any way for us to resolve this issue, or is the vulnerability checking basically unusable for these maven packages?
-
Hi @davi-morris_9177 ,
Unfortunately, the source data for these particular vulnerabilities specify invalid version numbers. A valid Maven version is a 5-part number consisting of 1-3 integer segments (separated by a
.), an optional build number (prefixed with a-), and then an optional qualifier (another-). Following these rules,2.9.10.8, is invalid.Valid versions are semantically sorted, where as invalid versions are alphabetically sorted -- which is what's causing the big headache here, since
"2.21.1" < "2.9.10.8"when you sort alphabetically.At this time, we don't have any means to "override / bypass" source data, and rewriting/updating our Maven version parsing for just a small corner case (i.e. these old/irrelevant vulnerabilities in particular) doesn't seem worthwhile.
As such, for the time being, your best solution is just to "Ignore" these vulnerabilities via an assessment. They are totally irrelevant now, not just because they refer to ancient versions, but there is simply no realistic real-world exploit path: https://cowtowncoder.medium.com/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062
FYI - for ProGet 2026, we are working on a lot of improvements in vulnerability management that will reduce the noise of these non-exploitable vulnerabilities so teams can address actual risk and focus on delivering value instead of constant patching.
Thanks,
Alana