Welcome to the Inedo Forums! Check out the Forums Guide for help getting started.
If you are experiencing any issues with the forum software, please visit the Contact Form on our website and let us know!
Error Trying to add new User Directory (Active Directory LDAP)
-
Hey Guys,
I'm Running ProGet 5.3.17 on a Docker host and I'm trying to configure an LDAP/AD connection for user authentication.
I'm following these instructions: https://docs.inedo.com/docs/various/ldap/advanced
But when I try to add an "Active Directory (LDAP)" connection I get the following blank screen:
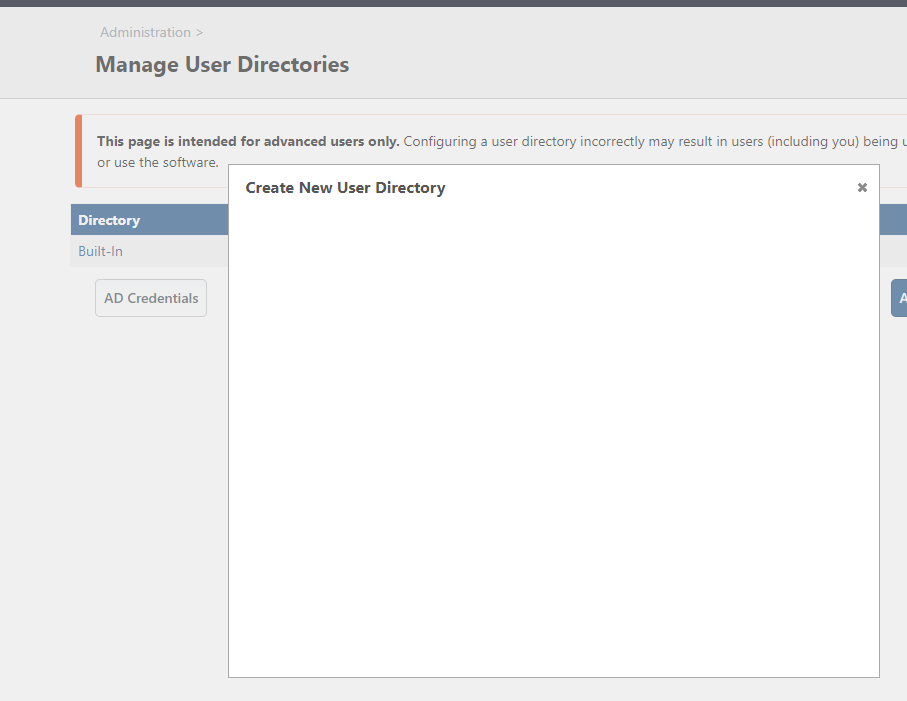
The error log shows this:
An error occurred in the web application: Could not load file or assembly 'InedoCore, Culture=neutral, PublicKeyToken=null'. The system cannot find the file specified.Details:
URL: http://proget.xxxxx.com/administration/security/directories/edit?type=Inedo.Extensions.UserDirectories.ADUserDirectory%2CInedoCore Referrer: https://proget.xxxxxxx.com/administration/security/create-new-directory User: Admin User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.66 Safari/537.36 Stack trace: at System.RuntimeTypeHandle.GetTypeByName(String name, Boolean throwOnError, Boolean ignoreCase, StackCrawlMarkHandle stackMark, ObjectHandleOnStack assemblyLoadContext, ObjectHandleOnStack type, ObjectHandleOnStack keepalive) at System.RuntimeTypeHandle.GetTypeByName(String name, Boolean throwOnError, Boolean ignoreCase, StackCrawlMark& stackMark, AssemblyLoadContext assemblyLoadContext) at System.Type.GetType(String typeName, Boolean throwOnError) at Inedo.Web.HttpArgs.QualifiedTypeQueryStringArgumentAttribute.ConvertFromString(Type targetType, String value) at Inedo.Web.HttpArgs.QueryStringArgumentAttribute.ConvertFromStringInternal(Type targetType, String value) at Inedo.Web.HttpArgs.QueryStringArgumentAttribute.Decode(String argumentName, Type targetType, HttpContext context) at Inedo.Web.HttpArgs.HttpArgumentProvider.HttpArgumentPage.InitializeArguments(IHttpHandler handler, HttpContext context) at Inedo.ProGet.WebApplication.ProGetHttpModule.PostMapRequestHandlerAsync(HttpApplication app) in C:\InedoAgent\BuildMasterTemp\192.168.44.60\Temp\_E82850\Src\ProGet.WebApplication\ProGetHttpModule.cs:line 437 at Inedo.Web.AhWebMiddleware.InvokeAsync(HttpContext context)My extensions look like this:
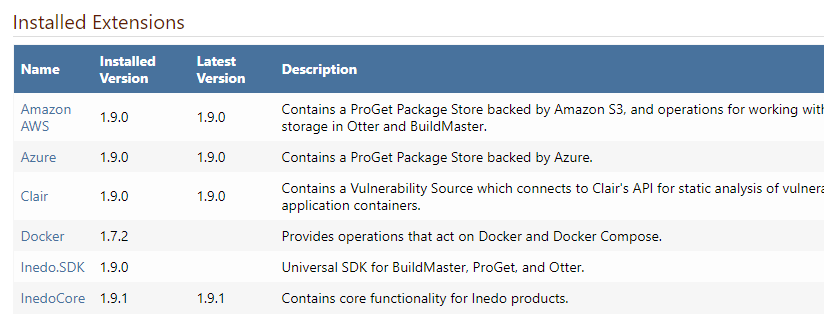
And advanced settings look like this:
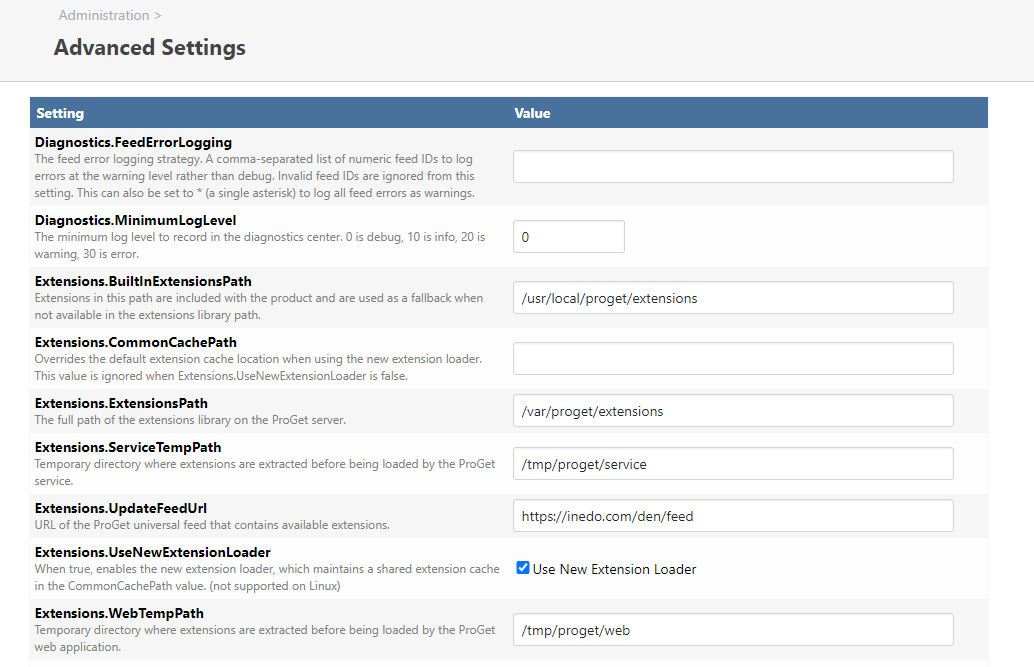
Any ideas?
Thanks
Simon
-
Hi Simon, based on what I'm seeing, it looks like the InedoCore extension didn't load, which is what would happen in this case...
Can you try restart container?
On the Admin > Extensions> What do you see on the
InedoCorepage? There should be a list of extensible components presented, including the directory type...
-
Hi @atripp
I have/did restart the container but no change:
This is the InedoCore extension page:
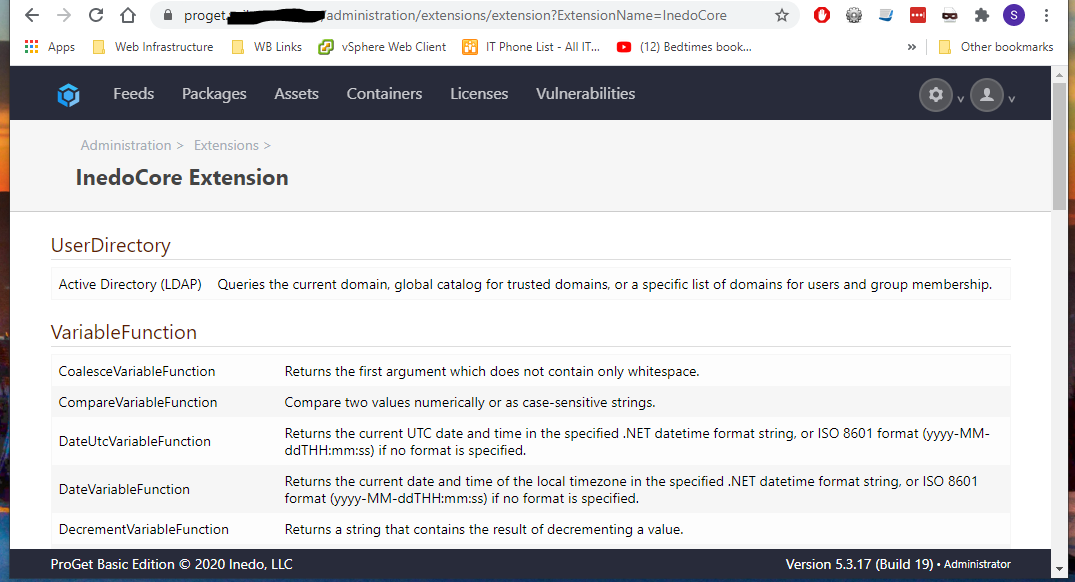
Thanks
Simon
-
Hi @scroak_6473,
I was able to recreate your issue. I think this may be an issue with the .NET 5 version of ProGet and creating a new Active Directory (LDAP) user directory. If one is already created, I do not have any issues editing it.
As a workaround, I would suggest changing over to the
progetmonoimage and create the new user directory, then change back to theprogetimage to configure it.I will reply back when I have an update on a proper fix for this.
Thanks,
Rich
-
Thanks @rhessinger
Can confirm this workaround works.
However it looks like you guys still are not supporting LDAPS, I have another forum post here: https://forums.inedo.com/topic/3024/proget-docker-image-ldap-ldaps-support?_=1607379833333
Do you know if LDAPS in a docker container image will ever be supported?
Thanks
Simon
-
Glad to hear the workaround works. We are still currently working on the issue to fix the Add New functionality in .NET 5. To the best of my knowledge, LDAPS is currently working and we have users that are using it currently. Can you please tell me what issue you are having with LDAPS?
Thanks,
Rich
-
Hey @rhessinger,
I get the following error when selecting "use LDAPS":
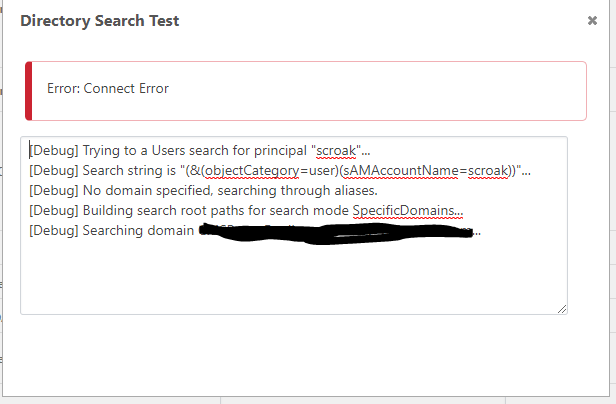
Unchecking the LDAPS box results in a successful connection/test.
My guess is that the docker image is unable to verify the SSL certificate of the LDAPS server, as the docker host is a Linux VM so it does not have a "root CA" certificate installed on it to verify the SSL cert of the domain controller.
Most other containerized applications all you to "skip the verification" like this example from Portainer:
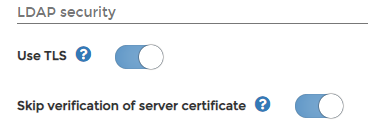
My previous forum post (linked to above) was a request to add this feature.
Alternatively if there if you guys can reference a root CA certificate that is installed on the containers file system I can see if I can "mount" it in the correct location. You'll just need to let me know where the certificate needs to be installed.
Additionally could you let me know the .Net 5 library you are using to provide this LDAP functionality?
Thanks
Simon
-
@rhessinger additionally the "Create new user directory" white screen "bug" above also happens when you try to add a new (clair) Vulnerability source:
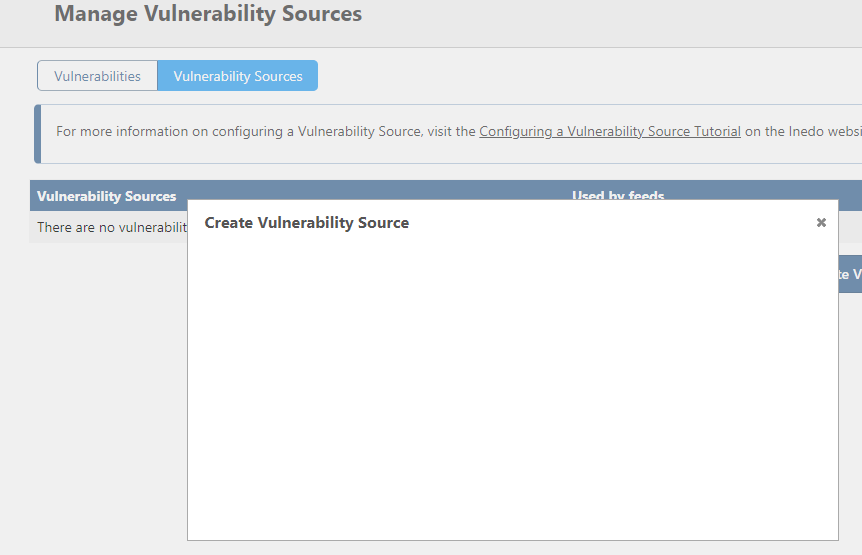
Thanks
Simon
-
Hi @scroak_6473,
For the add new User Directory and add new Vulnerability source, we have identified the issue and we are currently investigating the cause of it. It has to do with changes in .NET 5 for parsing types from strings. I will update this when we have a bit more information on it.
As for the AD stuff. That is definitely the issue, the LDAPS certificate is not being viewed as a valid certificate. I think we will need to investigate this further on how to bypass certificate validation. I would prefer you to open a new thread to discuss this issue with LDAPS in Docker. To answer your question, our code for connecting to Active Directory exists on GitHub in the inedox-InedoCore extension. It also includes a windows application for testing AD connections, including LDAPS. The library we are using on .NET 5 is
Novell.Directory.Ldap.NETStandard. For the .NET 4.5.2 target, we use the typicalSystem.DirectoryServices. We always encourage Pull Requests with fixes for this also!Hope this helps!
Thanks,
Rich
-
Hi @scroak_6473,
We have fixed the issue with creating new AD User Directories and vulnerability sources in .NET 5. It is set to release in ProGet 5.3.19 which is due out December 18, 2020.
Thanks,
Rich